Website security is a critical concern for every website owner. It’s much like securing a physical store or a house from burglars. Here’s why:
- Google blacklists around 10,000+ websites every day for malware and around 50,000 for phishing every week.
- Google displays an average of 4,352,659 browser warnings per week about hacked websites.
- Website owners take an average of 15 days to clean up their sites after receiving notifications that their sites have been compromised.
- 19% of the websites end up getting reinfected.
All this because website security is not a plugin.
The website works 24×7 and even when no one is watching or visiting, there’s a lot of activity happening in the background and the foreground. There are tasks being executed by the server and the search bots indexing the site etc. In all this there’s one special segment of bots (and humans) who are just attempting to break into the site. Why? Probably because no one is watching.
But someone is always watching.
Table of Contents
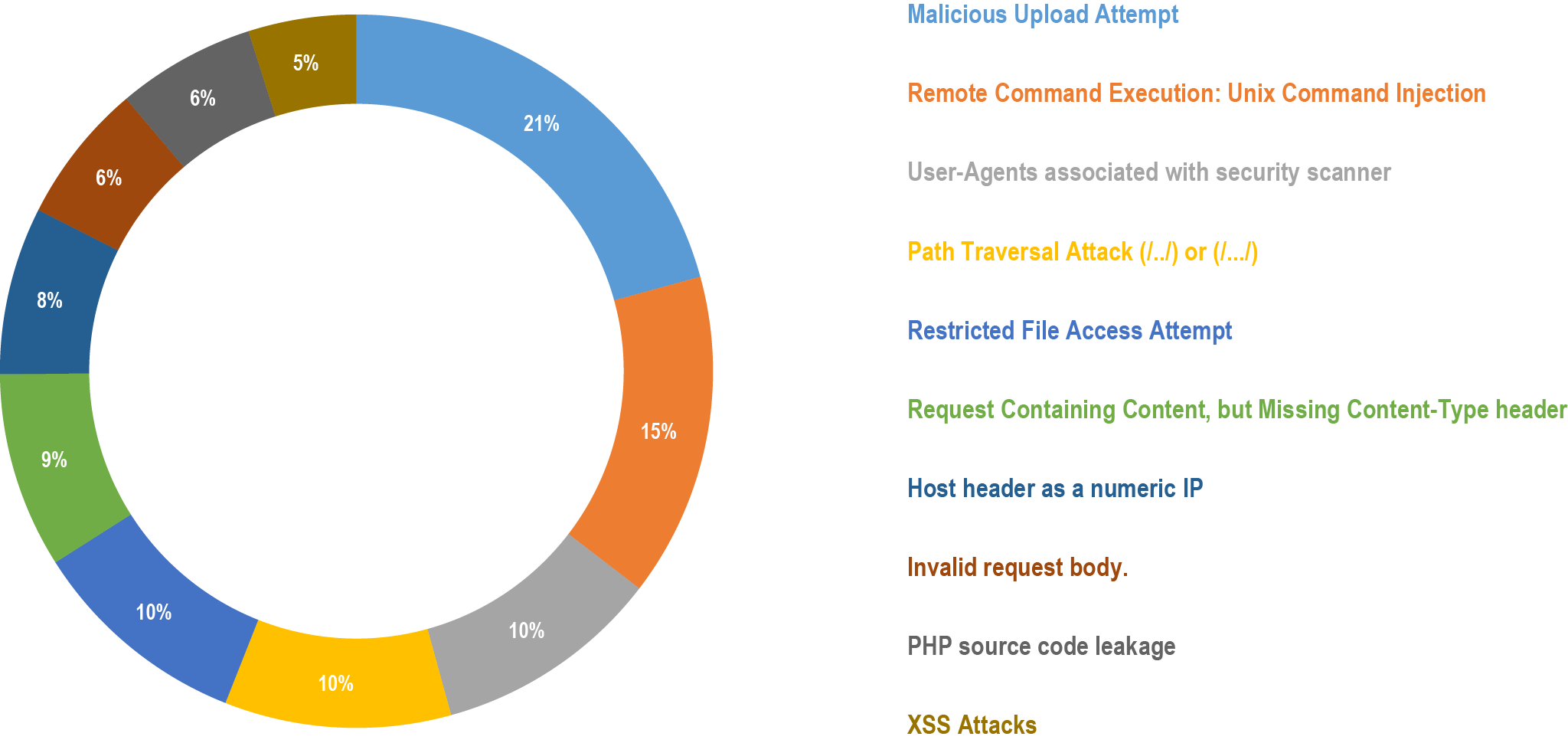
Here’s What the Firewall-Logs Say for the Year 2022 So Far:
Why Would Someone Hack Your Website?
There are several factors involved. If your website is doing anything great, there’s a good chance someone wants a piece of it. So the following are the major ones:
- To hijack your website traffic / visitors to their own website.
- Hijacking your search engine results without you knowing it (cloaking).
- Stealing the data stored in your website like customers’ emails, credit-cards etc.
- Bringing down your website by using up all the server-resources or just pure criminal mindset to deface the website etc.
We do however have an instance wherein one person (hopefully) announced on a social-media platform that the following websites were to get hit by DDoS attack starting in the next few hours until the websites went down. And as much as we’d like to think of this as a science experiment, this was pure hooliganism.
What is the business impact of a website security breach?
Essentially when one of the above happens, the business gets impacted in one or more of the following ways:
- Visitors from search engines land up on a site they were not expecting… end up purchasing from an incorrect brand / product.
- End up killing your website’s search-engine ranks. Once the SEO takes a hit, it would take months to recover.
- The stolen data will be misused by the hackers. You could even be legally liable.
- Your website is down for business.
So essentially these include financial losses, brand reputation issues and loss of search engine rankings.
Website Security Checklist — Securing Website From Unintended Mistakes
1. Enforce the policy of Least Privilege
In information security, computer science, and other fields, the principle of least privilege (PoLP), also known as the principle of minimal privilege or the principle of least authority, requires that in a particular abstraction layer of a computing environment, every module (such as a process, a user, or a program, depending on the subject) must be able to access only the information and resources that are necessary for its legitimate purpose.
Think: Who has access to your web-hosting, your website backend and what kind of access do they have and need…
2. Limit access to your website hosting control panel.
3. Use strong password for your website hosting control panel.
4. Limit access to your website’s backend.
5. Use strong password for your website’s backend.
What is a strong password?
- The one you can remember; and…
- Has a combination of numbers, uppercase, lowercase letters, at least one special character (which is not a space).
- Is at least 8 characters in length.
- Build a strong password
Let’s make a strong password:
- The name of your workplace / kids / pet: “Fireside”
- How do you feel about it: “like”
- What your year of appointment: let’s take 19 of 2019.
- Result: I-like-Fireside19
- Add some twist by replacing regular characters with lookalike numbers and special-characters: 1-l!k3-F!r3$!d319
- Smart thing to do: Build your own unique password instead of copying the above!
6. Access your website’s backend / hosting only from a secure and uninfected computer. Use a good antivirus software that has on-Access scanning. Additionally run a virus-scan regularly.
7. Confirm that you revoke access to your website once your web-developer, in-house support no longer require access. This also consolidates accountability in addition to access.
8. Avoid storing passwords or access details.
9. Implement Two-factor authentication (2FA) where possible. What’s 2FA?
Two-factor authentication (2FA) is a method of adding additional security to your account. The first “factor” is your usual password that is standard for any account. The second “factor” is a verification code retrieved from an app on a mobile device or email / computer etc.
Website Security Checklist — Securing From Webhosting Gotchas
10. Does your webhost provide a well-secured hosting environment? When were they in the news the last time for a security incident? A good webhost will ensure that the hosting configuration and software stack is well-setup and well-maintained including timely software updates. Ask them how often do they upgrade their software.
11. Disable directory indexing and browsing.
12. Host one website per account / container. Multiple website must be stored within their own container or user access. This prevents websites from cross-contamination.
13. Limit access to services like FTP, SFTP, SSH, MySQL, databases etc.
Website Security Checklist — Website Configuration
14. Avoid using defaults while installing the website or when deploying the settings.
15. Serve your website only from HTTPS and implement redirects from HTTP.
16. Avoid using admin as the WordPress username.
17. Follow security best practices like changing your WordPress-login-URL and using WordPress security plugins to safeguard your installation.
18. Use a Web-Application-Firewall (WAF) to stop attackers in their tracks.
19. Install timely software, plugin, extension, CMS updates. This is critical as zero-day vulnerabilities (amongst others) are addressed by these updates.
20. Disable file-editing. Some CMS implementing file-editing, claimed as a feature but obscure at best. How to Disable File Editing in WordPress.