
In one of the recent malware cleanups, we came across a situation where all the plugins were infected. Each of the JavaScript files inside the plugins had malicious code and there were over 800 infections. In this scenario you simply can’t take the time to fix each file one at a time. You have to repair the infected plugins to make sure there is no malicious payload leftover.
Working with command line interface using WP-CLI makes this task quick and easy. The idea is to delete all the plugins on the site and then install and activate previously active plugins. All this can be easily managed via WP CLI wp plugin command. It comes in handy for managing plugin related tasks like install, uninstall, activate, deactivate, delete, update, etc.
Note: This process will only re-install plugins from the WordPress repository. Third-party plugins will not get reinstalled.
Here is a step by step process to reinstall the plugins:
List Plugins and (Optionally Save the List)
You can run the following command to list all the installed plugins (active as well as inactive).
wp plugin list
This above command displays the number of installed plugins in your WordPress site in a table, including information such as the plugin’s slug, activation status, current version and available updates (if any).
Table of Contents
1. List Active Plugins
We are interested in listing all the active plugins so that we can reinstall and activate them. So we will use the following command:
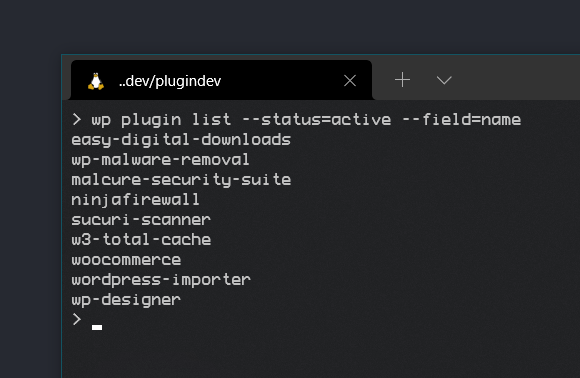
wp plugin list --status=active --field=name
Output: A list of active plugins
2. Create bash / shell script
Copy the above output and do some find and replace magic with multi-cursor or regex to add wp plugin install before each line. Search for ^ and replace with wp plugin install And add --force --activate after each line. Search for $ and replace with --force --activate.
Convert this file into a bash / shell script by adding the shebang #!/bin/bash.
Your file should look like this:
#!/bin/bash wp plugin install easy-digital-downloads --force --activate wp plugin install wp-malware-removal --force --activate wp plugin install malcure-security-suite --force --activate wp plugin install ninjafirewall --force --activate wp plugin install sucuri-scanner --force --activate wp plugin install w3-total-cache --force --activate wp plugin install woocommerce --force --activate wp plugin install wordpress-importer --force --activate wp plugin install wp-designer --force --activate
The above script installs and activates 9 plugins.
Save this file in the root of your WordPress installation (and delete it afterwards). You can call the script whatever you want but it’s advised to keep the sh extension which indicates it’s a shell script, in our case a bash shell script. We will name it install-plugins.sh. Next, we need to run the following command in the terminal to make it executable:
chmod +x install-plugins.sh
3. The Nuke Command: Delete the plugins
We will delete all the existing plugins on the WordPress install. We really don’t need inactive plugins, do we?
wp plugin delete --all
4. Batch Install WordPress Plugins Using WP-CLI Bash Script
Install and Activate Plugins
Now we will go ahead and install and activate plugins that were previously active. Just issue the following command to call the script we created earlier:
./install-plugins.sh
OR, optionally can use the following command for individually installing and activating each of the plugins, the tough way
wp plugin install plugin-name --force --activate
Creating and executing a bash script is a very powerful, simple, and easy way to perform multiple operations with one command.
WordPress core infected? Here’s a step-by-step guide to reinstall infected WordPress core the right way!
Happy coding!
See Also:
- Understanding and Resolving the Vuln.php Recurring Malware Issue
- Download WP CLI Temporarily & Using With Custom PHP Versions
- How to use Regex with WP CLI to Search & Replace WordPress Database
- YourService-Live & AdsNet-Work — Website Redirect-Causing JavaScript
- How to Fix a Blank WP-Admin Page in WordPress — A Comprehensive Guide