
During an internal audit of the WordPress plugins, the security researchers at Jetpack discovered two serious vulnerabilities in the All In One SEO Plugin. The same was disclosed by Marc Montpas on December 14, 2021. The patched version 4.1.5.3 was released on 8th December 2021. However the plugin has not been updated on all the 3+ million sites. According to plugin download statistics for the last two weeks since the patch was released, there are still more than 820,000 sites exposed to attacks.
The WordPress changelog for the plugin reads:
New in Version 4.1.5.3
Updated: Security hardening for REST API endpoints
Table of Contents
Security Vulnerabilities in WordPress All in One SEO plugin: Privilege Escalation & SQL Injection (SQLi)
Authenticated Privilege Escalation vulnerability
- Affected versions: Every version between 4.0.0 and 4.1.5.2 inclusively.
- CVE-ID (Common Vulnerabilities and Exposures ID): CVE-2021-25036
- CVSS Score: 9.9
Here’s the vulnerable code in All In One SEO WordPress plugin allowing for privilege escalation:
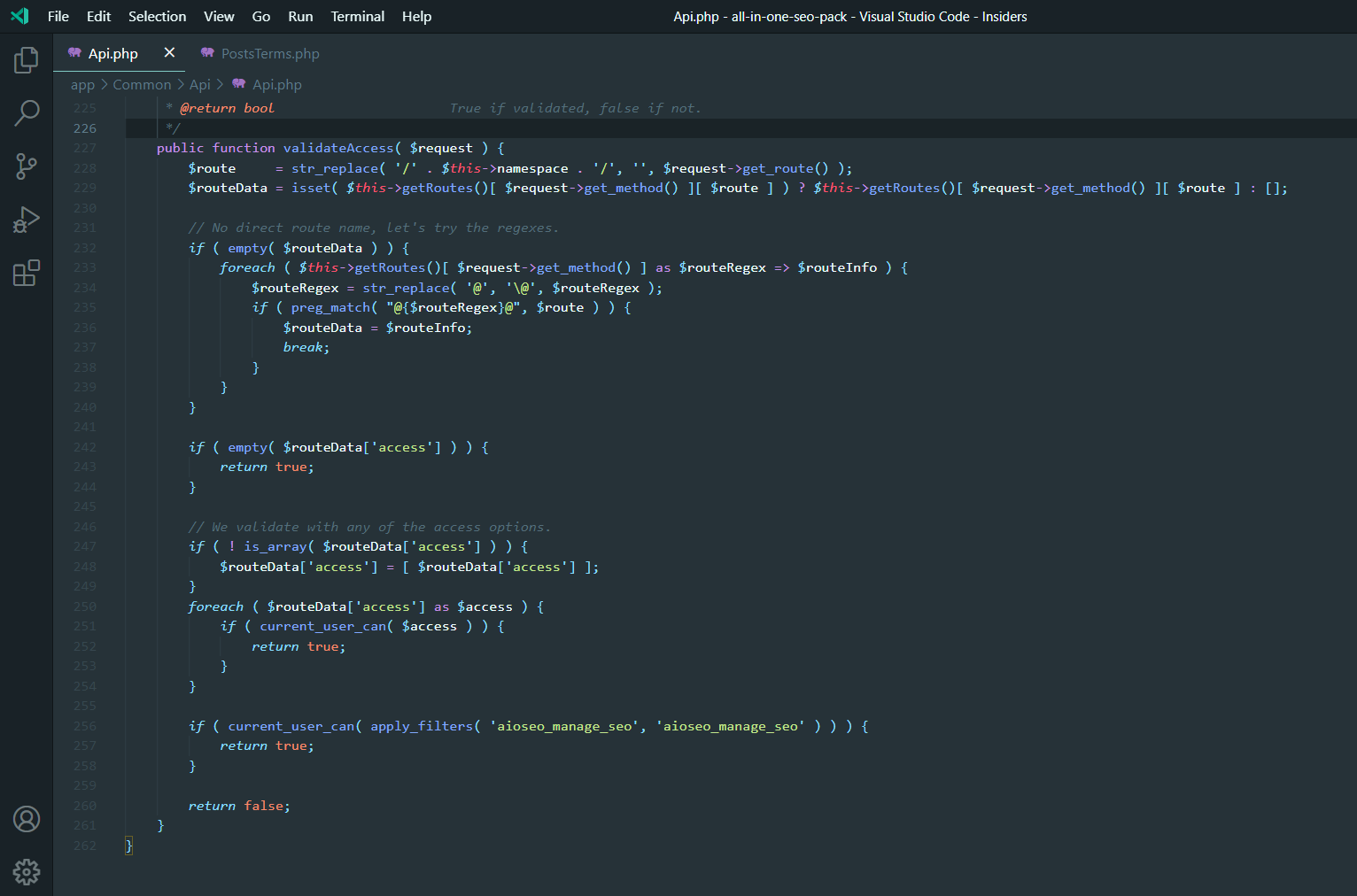
Authenticated Privilege Escalation vulnerability exploits the WordPress REST API, allowing an attacker to access usernames and passwords.
According to Jetpack:
“The privilege checks applied by All In One SEO to secure REST API endpoints contained a very subtle bug that could’ve granted users with low-privileged accounts (like subscribers) access to every single endpoint the plugin registers.
…Since it didn’t account for the fact that WordPress treats REST API routes as case-insensitive strings, changing a single character to uppercase would completely bypass the privilege checks routine.”
As such when exploited, this vulnerability has the capability of effectively giving backdoor access to any attacker and enabling them to overwrite certain files within the WordPress file system. This would even help the attackers elevate the privileges of subscriber accounts (or other low privilege roles) to admin account.
Authenticated SQL Injection
- Affected versions: Every version between 4.1.3.1 and 4.1.5.2 inclusively.
- CVE-ID (Common Vulnerabilities and Exposures ID): CVE-2021-25037
- CVSS Score: 7.7
Here’s the vulnerable code in All In One SEO WordPress plugin allowing for SQL injection:
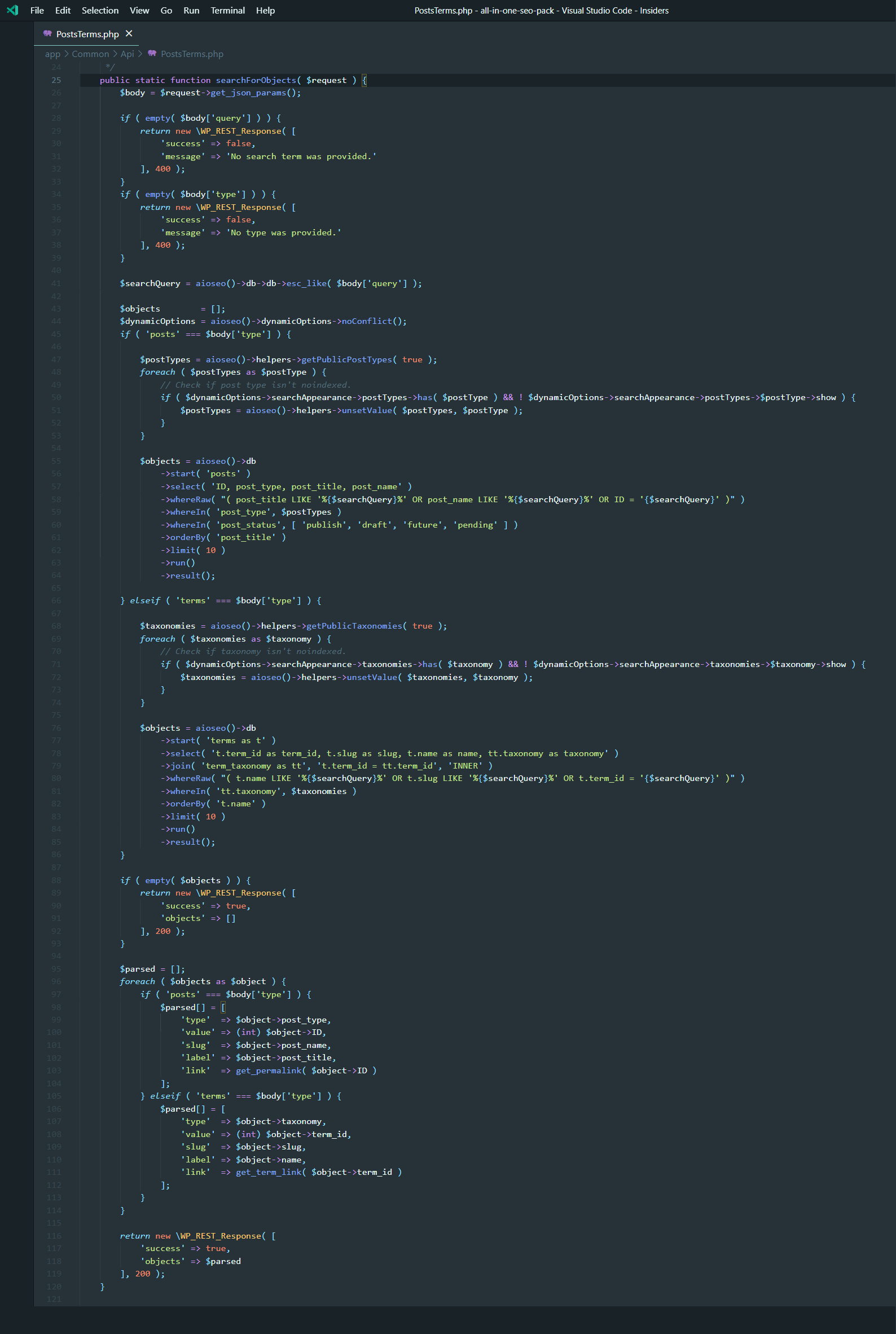
As per Sucuri,
The second vulnerability discovered is caused due to a particular endpoint located here:
/wp-json/aioseo/v1/objects
By default this endpoint is not intended to be accessible by low-level accounts. However, due to Authenticated Privilege Escalation vulnerability in the plugin, the attackers could first elevate their privileges and then execute SQL commands to leak sensitive data from the database, including user credentials and admin information.
This chained exploit has the capability of leaving the websites open to threat of takeover by establishing a backdoor on the web server.
Recommendation: Updating All in One SEO Plugin
The highest at risk would be the sites that allow user-registration / sign-ups like ecommerce websites using WooCommerce, Easy Digital Downloads and other mambership solutions as these allow visitors to create their own account on the site.
Is you site still running versions <= 4.1.5.2 of WordPress All in One SEO plugin? It’s time to update to the latest version and also run the following checks to be on the safe side:
- Review all the user accounts; especially the administrator users in your WordPress dashboard and remove the suspected ones.
- Change the passwords for all the administrator accounts.
- If you are running an e-commerce or membership site, do change WordPress salts and request all your users to update their passwords.
- Last but not the least, run a complete website scan using our malware scanner to make sure there are no signs of infection.