
One of our clients reported that users on their website had been receiving spam mail containing fake invoices. Not only that, the subject of the mail contained the website’s title giving an impression that the mail was related or possibly sent with work pertaining to the website.
Symptoms of Mailchimp Ursnif Gozi Banking Trojan
The rogue mail contained a link to download a zip file.
Here’s an example mail the client forwarded:
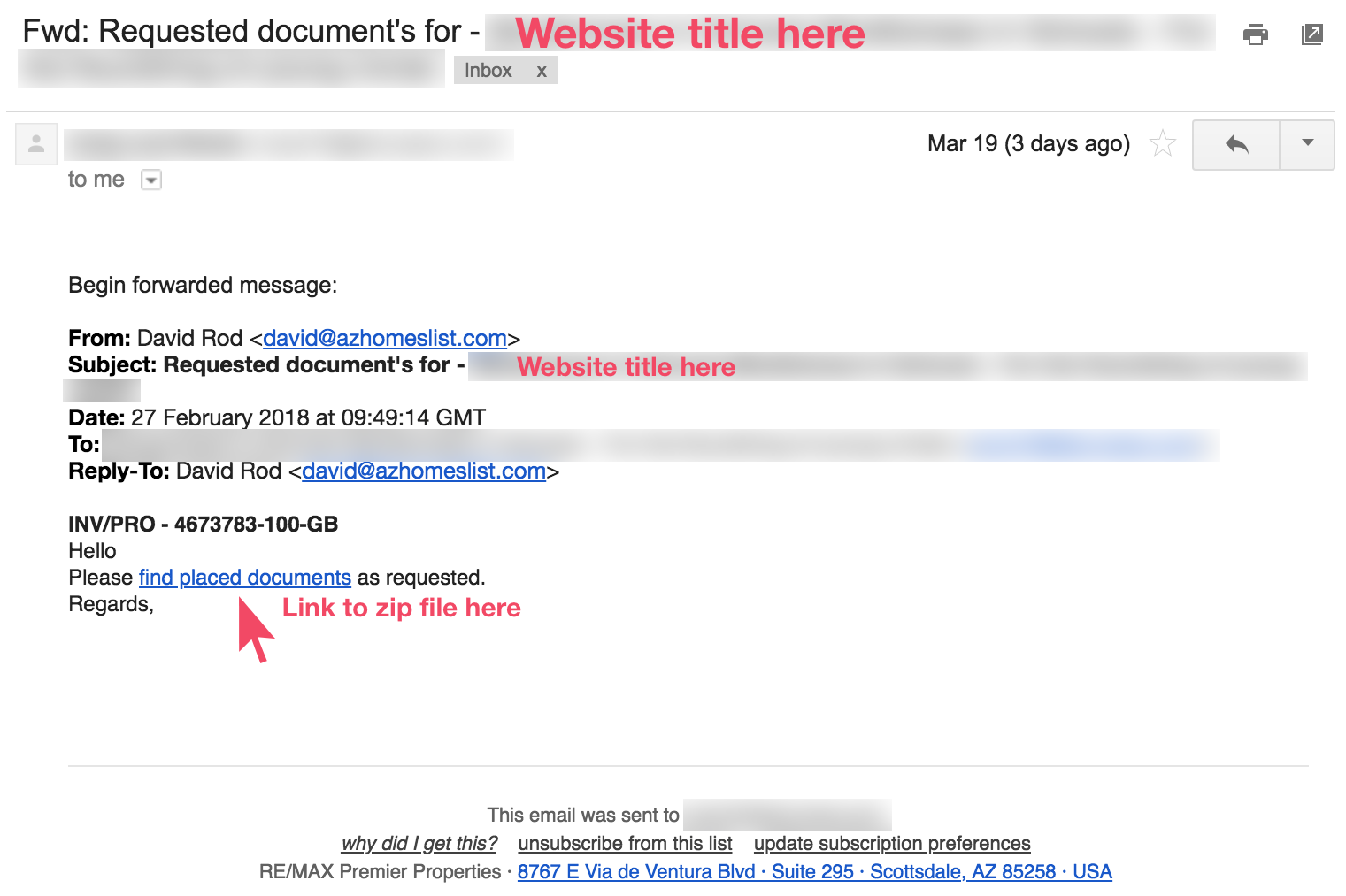
While spam is not unusual or surprising, one of the users who registered on the website reported that they had created a new email address and had never used it anywhere else. A quick Google search led to My Online Security website article containing the details.
Manual Inspections
Time to go digging.
Server and the hosted files were manually reviewed on a per-site, per-plugin, per-script basis for thoroughness. None of the files were found to be infected. A thorough security audit revealed several gaps but none indicating an infection or a compromised website (check this article for key signs that your site is infected). However after looking some more it was apparent that the affected emails were publicly visible.
Evidently a web scraper had scraped the entire website and extracted the emails from the website and added them to the Mailchimp list. This is what can happen if website configuration and security is taken lightly.
Mailchimp makes it easy to bulk upload email addresses to mailing lists—all you need is a list of emails and you can just upload and start spamming without any confirmation from the recipient.
A well-maintained and well-configured site typically does not warrant security hardening. However it is strongly recommended that sites storing user-information or sensitive, business-critical data must undergo security hardening. If you feel your website is hacked, do not panic. Here’s how to recover your hacked WordPress website.
Customer education is paramount to security awareness, yet it’s still considered an afterthought… unless disaster strikes. Are you protected?