
So, this one takes days to impact, weeks to detect and months to get off blacklists. Essentially any website-driven business dies because of months of impact.
Recently, one of our customers reported her site as infected. Following the usual protocol, we ran various types of scan via WordPress plugins and even some Linux anti-virus software. Detection: nada… zilch!
Root-Cause
Apparently, not an scanner on earth would detect what’s wrong with the website. The site essentially was clean.
Avast One reported the site as phishing. The site had a brandname with .info in the domain name. There was a competitor with the same brandname but with a .com in the domain name. Could that be the issue?
Avast One even popped up while working in the WordPress Admin Dashboard wp-admin area.
While we monitored the site… soon McAfee Webadvisor started flagging the site as Risky and containing PuPs — Potentially Unwanted Programs.
Looking into Google Transparency Report — Safe Browsing site status, the site was clean.
Problems With Detection
So essentially:
- The scanners detected nothing.
- Google detected nothing.
- The site was getting flagged by multiple vendors — all for weird, random, unknown reasons.
What in the world…!
So the only thing left was to go back to the drawing board.
How do various security-vendors collect the data? Without getting technical about it:
- These security vendors have no access to the WordPress backend (exception: antivirus browser-plugins).
- They rely on user-submitted reports.
- Scanning website content which is publicly available.
Check & Analyze SERPs
We put ourselves in these shoes and ran a Google Site-Search on the affected site… lo and behold… Voila! Digging a few SERPs deeper, the site had PDFs indexed and some of them weren’t some a site-owner would expect.
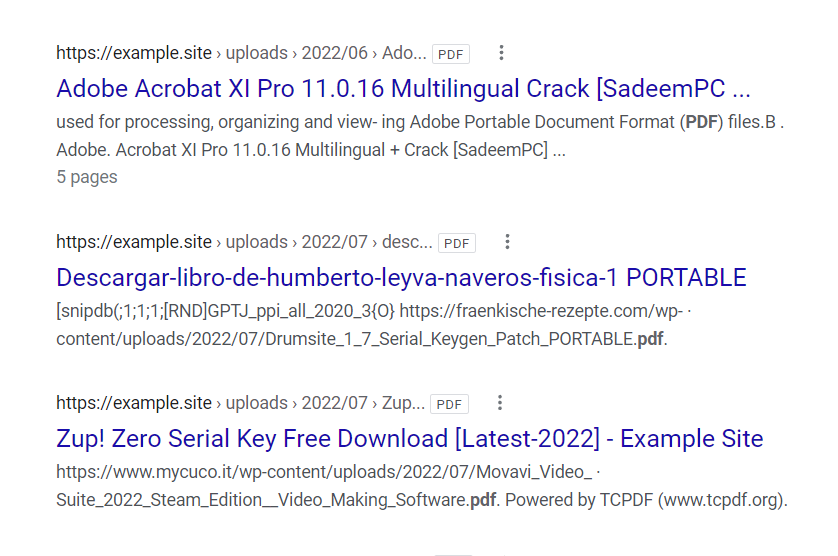
Final Findings
Now let’s take a few steps back and see what happened:
- A rogue user registered on the website.
- The user had the ability to upload PDFs on the website.
- The uploaded PDFs would have taken a few days to get indexed.
- The site would have been flagged by one security vendor and then the next.
- No malware scanner was able to detect these suspicious PDF uploads.
- The site would take a long time to be taken off multiple blacklist.
As you can see, this is one unusual and super-tricky case wherein a website would have killed a business without leaving any clue.
See Also:
- Understanding and Resolving the Vuln.php Recurring Malware Issue
- How to Fix a Blank WP-Admin Page in WordPress — A Comprehensive Guide
- Step-by-Step Guide to Cleaning Up Massive JavaScript Malware Redirects NDSW / NDSX / NDSJ
- Elon Musk, Apple, Bill Gates and Other High Profile Twitter Accounts Hacked in Cryptocurrency Scam
- Download WP CLI Temporarily & Using With Custom PHP Versions