The Japanese Keyword Hack injects thousands of spammy Japanese pages into your website. They’re usually invisible to normal visitors but fully visible to Google. The result? Search results stuffed with junk, rankings tank, and your credibility takes a hit. This guide walks you through exactly how to find and remove Japanese SEO spam from your WordPress website, and how to make sure it doesn’t come back.
Table of Contents
- What Is the Japanese Keyword Hack?
- Telltale Signs of the Japanese Keyword Hack
- Diagnosing the Japanese Keyword Hack
- Step-by-Step Guide to Fix Japanese SEO Spam
- Step 1. Take a Complete Backup
- Step 2. Remove Unauthorized Google Search Console Accounts
- Step 3. Scan Your Website for Malware
- Step 4. Clean Infected Files and Database Entries
- Step 5. Review and Restore .htaccess and wp-config.php
- Step 6. Manually Investigate Malicious Sitemaps and Backdoors
- Step 7. Reset All Passwords and Remove Fake Admins
- Step 8. Update WordPress, Themes, and Plugins
- Step 9. Submit Your Site for Google Review
- Step 10. Harden Your Website Against Future Attacks
- Frequently Asked Questions
What Is the Japanese Keyword Hack?
The Japanese Keyword Hack — also known as Japanese SEO Spam — is a type of malware attack where hackers inject auto-generated Japanese content into your site. The purpose of these pages is usually to sell counterfeit goods like fake luxury items, electronics, or pharmaceuticals. In many cases, the spam links also redirect visitors to malicious or affiliate sites controlled by the attacker.
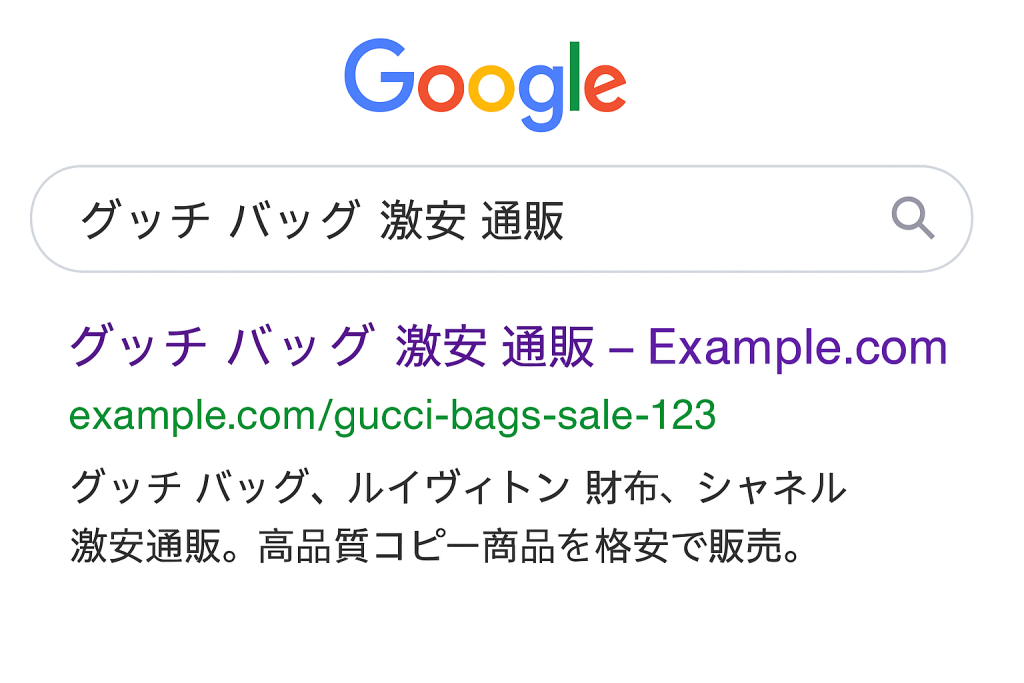
What makes this hack particularly tricky is cloaking. While your site may look perfectly normal to you and your visitors, Googlebot sees the injected spam content. This means your brand can appear in Google’s search results with Japanese titles and snippets even though you never published them.
The consequences include:
- Google search results show Japanese characters and unrelated content.
- Your legitimate rankings tank and organic traffic drops.
- Google Search Console flags your site under Security Issues or applies a Manual Action.
- Customers lose trust when they see hacked results tied to your brand.
Telltale Signs of the Japanese Keyword Hack
One of the most obvious warning signs of the Japanese Keyword Hack is when your website starts showing up in Google search results with content you never created. A quick search using the site:yourdomain.com operator often reveals dozens, sometimes even thousands, of strange URLs. Instead of your normal blog posts or product pages, you’ll see entries filled with Japanese text and links to unfamiliar products. These pages don’t usually appear on your site when you browse it directly, but Google indexes them because the spam is injected specifically for search engines.
Another red flag is an alert from Google Search Console. Many site owners discover the hack only after receiving a notice under the Security Issues tab or a Manual Action. Google may warn you that your site has been hacked, or that spammy pages are being served to search engines.
Sometimes the signs are more subtle. Hackers often tamper with your site’s infrastructure to keep the spam pages hidden and indexed. You may notice strange entries in your robots.txt file that point search engines toward malicious sitemaps, or you might come across entirely new sitemap files you never generated. These sitemaps are typically auto-generated and stuffed with thousands of spam URLs.
Another symptom is the presence of unfamiliar users or account changes. In WordPress, for example, you may find new administrator accounts you didn’t create. In Google Search Console, you may spot unauthorized property owners who’ve been added without your knowledge. Both the tactics are used by attackers to maintain control of your site even after you try to clean it up.
Diagnosing the Japanese Keyword Hack
Before you begin the cleanup process, it’s important to understand the full extent of the infection. The Japanese SEO Spam is notorious for using cloaking, which means what you see in your browser isn’t always what Google sees. A thorough diagnosis ensures you don’t miss hidden spam or backdoors. Here’s a step-by-step process:
1. Search Your Site on Google
Start with a simple Google search using the operator:
site:yourdomain.com

If the hack is present, you’ll often see dozens or even thousands of pages filled with Japanese characters and links to unfamiliar products. These pages usually don’t appear when you browse your site normally, but Google has indexed them because hackers specifically target search engines. This quick search is often the fastest way to spot the infection.
2. Inspect URLs in Google Search Console
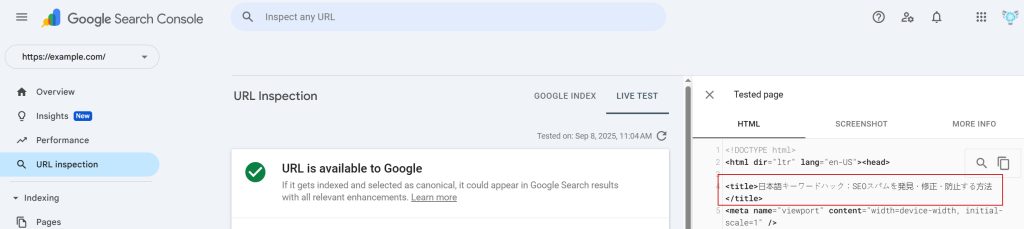
Once you’ve identified suspicious URLs, run them through the URL Inspection tool in Google Search Console. Compare the “Page HTML” that Googlebot sees with what you see in your browser. If the content doesn’t match — for example, Japanese text for Googlebot but normal content for you — that’s evidence of cloaking.
3. Test Live URL (Fetch as Google)
In Search Console, use the Test Live URL option (formerly “Fetch as Google”). This shows you exactly how Googlebot renders a page in real time. Hackers often serve different content based on the requesting User-Agent, so this test is one of the most reliable ways to uncover hidden spam. If Google’s rendering includes Japanese characters or injected links, the hack is confirmed.
4. Check with Different User Agents
Sometimes cloaking isn’t obvious in regular browsing but shows up when the site detects a specific user agent. Use Firefox browser addon User Agent Switcher to view webpages with various different user agents in your browser. If the page looks different when fetched as Google’s user agent versus as a regular browser, you’ve uncovered another sign of cloaking.
5. Check Your Server Files
Hackers often drop backdoors in your site’s file system. Inspect directories like wp-content/uploads where PHP files don’t normally belong. Look for recently modified files across your server, and carefully review .htaccess, php.ini, robots.txt, user.ini and wp-config.php for unauthorized redirects or injected code.
Step-by-Step Guide to Fix Japanese SEO Spam
Cleaning Japanese Keyword Hack needs to be a thorough process. Hackers often leave hidden backdoors, malicious database entries, and altered configurations that can re-infect your site if left behind. The key is to work systematically, addressing both the infection and the underlying vulnerability. Here’s a complete step-by-step guide:
Step 1. Take a Complete Backup
Before you make any changes, create a full backup of your WordPress site — both the files and the database. Even though this backup will include the malware, it’s a critical safety net. If something breaks during cleanup, you can always roll back. It also serves as a useful reference for comparing clean vs. infected files later. Store this backup securely, preferably off the server.
Step 2. Remove Unauthorized Google Search Console Accounts
In this type of attack, hackers typically add themselves as property owners in Google Search Console to retain control, even after you’ve removed malware from your site. This allows them to resubmit spammy sitemaps or manipulate your search appearance. Go to Search Console → Settings → Users and Permissions and carefully review the list. Remove any accounts you don’t recognize. This cuts off attacker access at the search visibility level and prevents them from undermining your cleanup efforts.
Step 3. Scan Your Website for Malware
It is very important to thoroughly scan the website files as well as database for malicious code and infections. It is strongly recommended to run both remote and server-side scans.
Remote malware scanners simulate how search engines see your site and can reveal cloaked spam that normal visitors miss. Use Malcure Webscan to scan your website’s source code for malicious links, redirects, iframes, JavaScript, and spam. There’s a caveat with remote scanners; they have limited access to server resources.
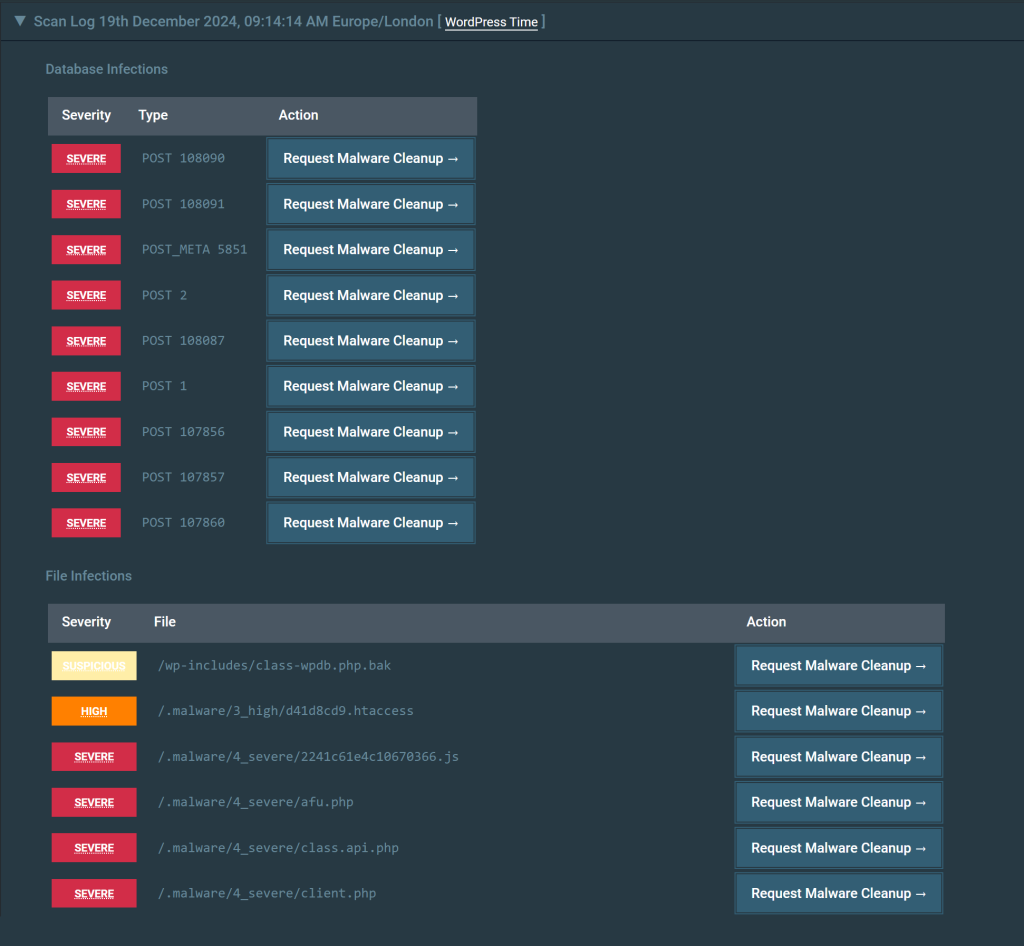
After running the remote scan, scan your site using server-side scan to dig deeper into files and databases to detect malicious scripts and hidden backdoors. Install Malcure’s Malware Scanner on your WordPress site and initiate a deep scan. It scans each and every file including backups, archives, images, hidden files, logs, etc. and database for malware.
Malcure Malware Scanner is the most precise WordPress malware scanner. It will detect all the infections and malicious code in WordPress file system as well as database entries. The best part is that the scanner scans the entire database. No manual inspection needed. It scans wp_posts, wp_postmeta, wp_comments, wp_commentmeta and wp_options tables which are common targets for injected entries. Just run the scan, Malcure Malware Scanner has got you covered.
Step 4. Clean Infected Files and Database Entries
Once the malware is identified, analyse and remove the injected code or replace compromised files with fresh copies from the official WordPress repository. For plugins and themes, reinstall clean versions from trusted sources. If spammy posts or pages were added to your database, delete them carefully. Avoid using automated “delete all” approaches — review each flagged item so you don’t accidentally remove legitimate content.
If you are using Malcure Advanced Edition you can delete and repair infected files directly from the WordPress dashboard.
Step 5. Review and Restore .htaccess and wp-config.php
The .htaccess, php.ini and wp-config.php files are prime targets for attackers. Malicious redirects, hidden rules, or injected code may be present. Compare these files against clean defaults from WordPress, and restore them if needed. Ensure there are no strange rewrite rules pointing search engines toward spammy sitemaps or cloaked content.
Step 6. Manually Investigate Malicious Sitemaps and Backdoors
One of the techniques employed by the hackers is to generate new sitemap files filled with spammy URLs to get their content indexed quickly. Search your root directory and subfolders for unfamiliar sitemap files (e.g., sitemap1.xml, sitemap_index.xml, etc.) and delete them. Also look for backdoor scripts — often disguised as innocuous PHP files in uploads or plugin folders. These give hackers ongoing access, so eliminating them is critical to preventing reinfection.
Step 7. Reset All Passwords and Remove Fake Admins
Change all your credentials: WordPress logins, hosting control panel, FTP/SFTP accounts, and database passwords. In WordPress, review the Users menu and remove any unauthorized administrator accounts. Hackers frequently create hidden admin users to regain entry even after cleanup. Removing them ensures they can’t sneak back in.
Step 8. Update WordPress, Themes, and Plugins
Outdated software is the number one reason sites get hacked. Once your site is clean, update WordPress core, all themes, and all plugins to their latest versions. Delete any unused or abandoned themes and plugins — if you’re not actively using it, it’s a potential liability.
Step 9. Submit Your Site for Google Review
After the cleanup, log in to Google Search Console and request a review. If your site had a “Security Issue” or “Manual Action” warning, you’ll need to submit a Reconsideration Request. Provide a short explanation of what was wrong and confirm that you’ve cleaned the infection. Once Google verifies the spam is gone, your hacked pages will gradually disappear from search results.
Step 10. Harden Your Website Against Future Attacks
Finally, take preventive measures to reduce the risk of reinfection. Install a trusted WordPress security plugin like Malcure Security Suite for automated scans. Enable a Web Application Firewall (WAF) to block malicious traffic. Enforce strong, unique passwords for all accounts, limit admin privileges, and enable two-factor authentication. Regularly scan your site and schedule automated backups so you’re prepared if anything goes wrong again.
Cleanup doesn’t end once the spam is gone. Keep monitoring your site logs, Search Console, and malware scanners for signs of reinfection. Rankings usually begin to recover within 2–6 weeks, though it can take longer if Google applied a manual penalty. Consistent monitoring ensures that if hackers attempt to re-enter, you’ll catch them before major damage is done.
Frequently Asked Questions
How did my WordPress site get hacked with Japanese keywords?
The Japanese Keyword Hack usually happens due to outdated plugins, vulnerable themes, weak passwords, or poor hosting security. Attackers exploit these weaknesses to inject malicious code, create spammy pages, and gain persistent access through hidden backdoors.
Will removing the Japanese keyword spam fix my Google rankings?
Yes, but recovery isn’t instant. It can take some time for Google to re-crawl and de-index spammy pages. Use the Removal Tool in Google Search Console for faster cleanup.
Once you remove the spam and request a Google review, rankings typically start to recover within 2–6 weeks. If a manual penalty was applied, it may take longer. Consistently monitoring your site after cleanup is essential for restoring search visibility.
Can I fix the Japanese SEO Spam hack without technical skills?
It depends on the severity of the infection. Basic steps like removing fake Search Console users and resetting passwords are straightforward. But cleaning infected files, databases, and backdoors often requires technical expertise. If you’re unsure, it’s safer to get professional malware removal help.
How do I know if my site is fully clean?
Run multiple scans — both remote and server-side — to ensure no infected files remain. Verify that no strange sitemaps, hidden admin accounts, or cloaked pages are present. Also, monitor Google Search Console for security warnings or reinfection alerts in the weeks following cleanup.
How can I prevent this hack from happening again?
Keep WordPress, plugins, and themes updated at all times. Remove unused software, enforce strong passwords, limit admin access, and enable two-factor authentication. Use trusted WordPress security plugins and enable a Web Application Firewall (WAF) to block malicious traffic before it reaches your site.
Following these steps will help restore your site’s security after a Japanese keyword hack (Japanese SEO Spam). If the hack persists or you’re unsure about handling WordPress files or databases, seek professional help for WordPress malware removal and cleanup.