
This is literally the easiest malware removal guide for WordPress on the internet. This is as easy as it gets.
Malware removal is covered in 5 simple steps:
- Inspection: Ascertaining that your website actually has malware.
- Lock-up & Lock-down: Update the website credentials.
- Clean Up: Detect and clean or remove the infected files.
- Root Cause Analysis: Review the infected files to get rid of root cause of malware infection.
- Securing: Harden security of the your WordPress website.
Table of Contents
1. Ascertaining that your website actually has Malware
Is your website redirecting to unwanted URLs? Or is it broken in some manner? Is it defaced? You can use the following tools to analyse your website and verify that the problem is actually malware and not an unintentional .htaccess or plugin issue.
- Google Safe Browsing Diagnostic
- Sucuri Website Malware Scanner
- VirusTotal Analyzer
- Geek Flare Screenshot Checker
- GeoPeeker Peek Results
It’s quite possible that you’d have faced one or more of the following:
- Your website host blocks your hosting citing malware on the site.
- You got a mail from Google Search Console that your site is infected.
- You got a mail from Google Ads that your site is infected.
- You find that your site is redirecting to some malicious URL or a visitor reports this to you.
- Your website URL shows Google warnings like “this site may harm your computer” or “deceptive site ahead”.
Other symptoms can include site-slowness, information from website access-logs / error-logs etc.
2. Website Lock-Up & Lock-Down
In this step we need to prepare for malware removal. Before we start the cleanup, we need to make sure no one else has access to the site else they’ll keep re-infecting the website and we’ll be in an endless loop.
- Put your website in maintenance mode.
- Remove admin access for all the other users and only retain one admin account.
- Change your WordPress password.
- Change your cPanel / FTP / MySQL passwords.
This is also a good time to do the following whilst you’re in the process of removing malware:
- Facebook Ads (You should pause your ads when your site is infected).
- Google Adwords (Turn Adwords off you’re just bringing potential first and only 1 time clients to bad user experience).
- Put up a notice on your Facebook, Instagram, etc notifying that your website is experiencing a problem and that you have someone looking into it.
- Put your website into maintenance and put up a notice that your website is being worked upon.
3. Malware CleanUp
The worst thing you can ever do with a hacked site is just restore a backup. Here’s why.
The top 5 reasons why restoring a backup first is wrong:
- Erases proof of the entry point.
- The backup usually contains the same vulnerability.
- Losses leads and sales made since last backup.
- Removes any logging plugins recorded leading up to the detection.
- In the event of criminal activities you damage evidence.
With our website in maintenance mode and no access to anyone else, let’s start the process.
- Download and install Malcure Malware Removal plugin from the WordPress plugin repository. The Malcure malware removal plugin is used by web-security agencies and professionals to find out the most troublesome malware. It checks core WordPress files as well as plugins installed from the WordPress repo for integrity. If a file has changed, it will report it as suspicious. The plugin will also scan all files for malware barring none. And the pro version of the plugin, Malcure Advanced Edition comes with WP CLI support which makes it a powerful beast when it comes to malware removal.
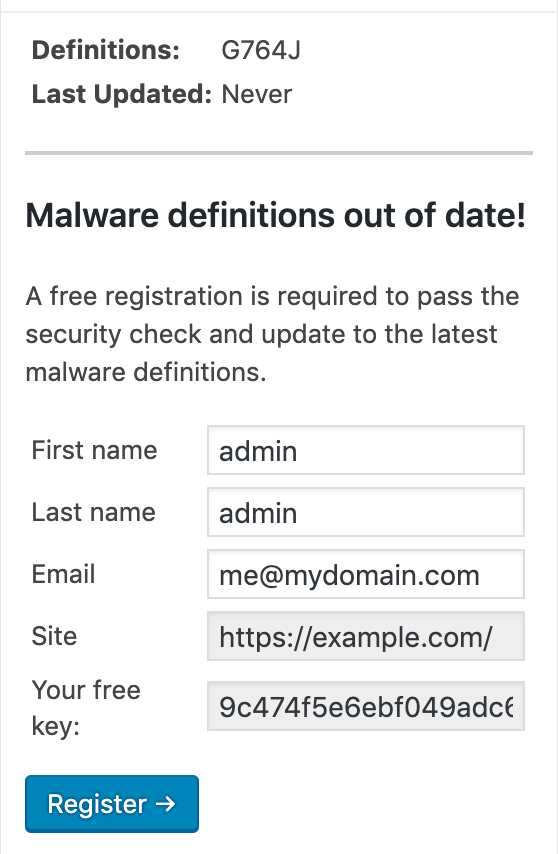
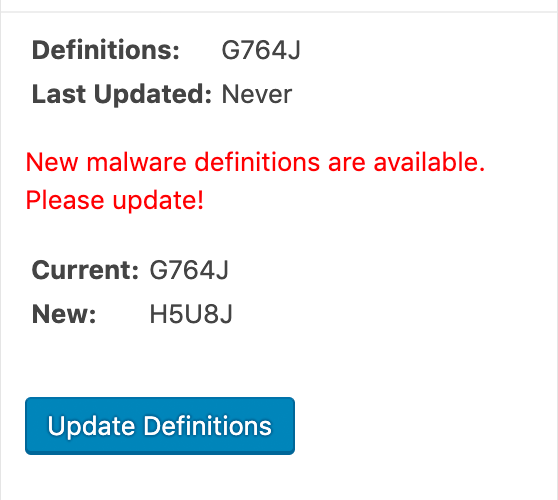
- Register the plugin for free to get the latest malware definitions. If you don’t have the latest malware definitions, the plugin will not be able to effectively detect the malware.
- Time to run the scan. Set the number of files to scan per request to a reasonable number. The higher number the faster the scan but the higher the website load. A sensible number is 20 files per request. Open the advanced settings box and check the box that says “Don’t show content matches”. Click the “Start Scan” button. If it hangs, try a smaller number like 10 or lower.
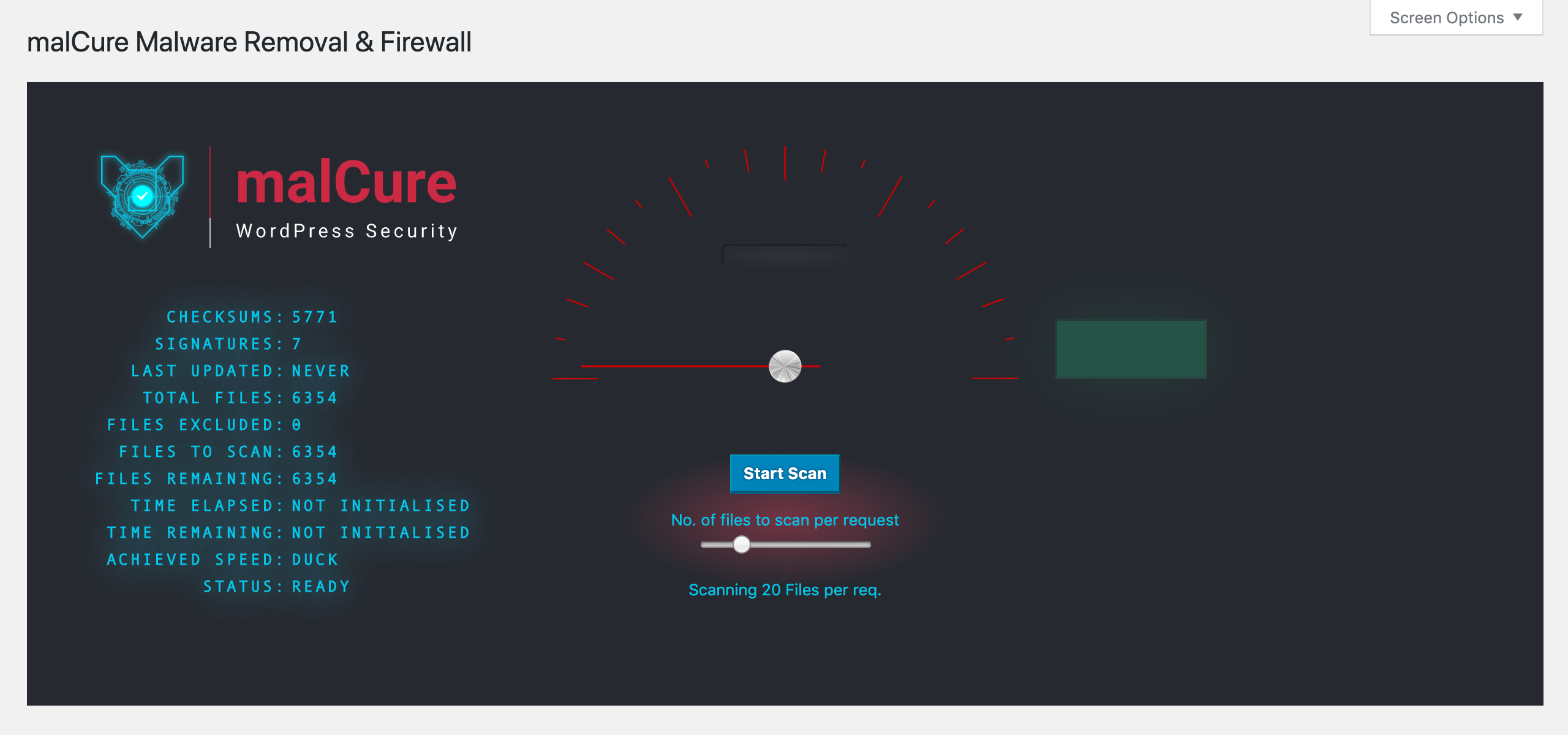 Click on the Start Scan button to initiate scan. The scan may take a while but will report the progress.
Click on the Start Scan button to initiate scan. The scan may take a while but will report the progress.
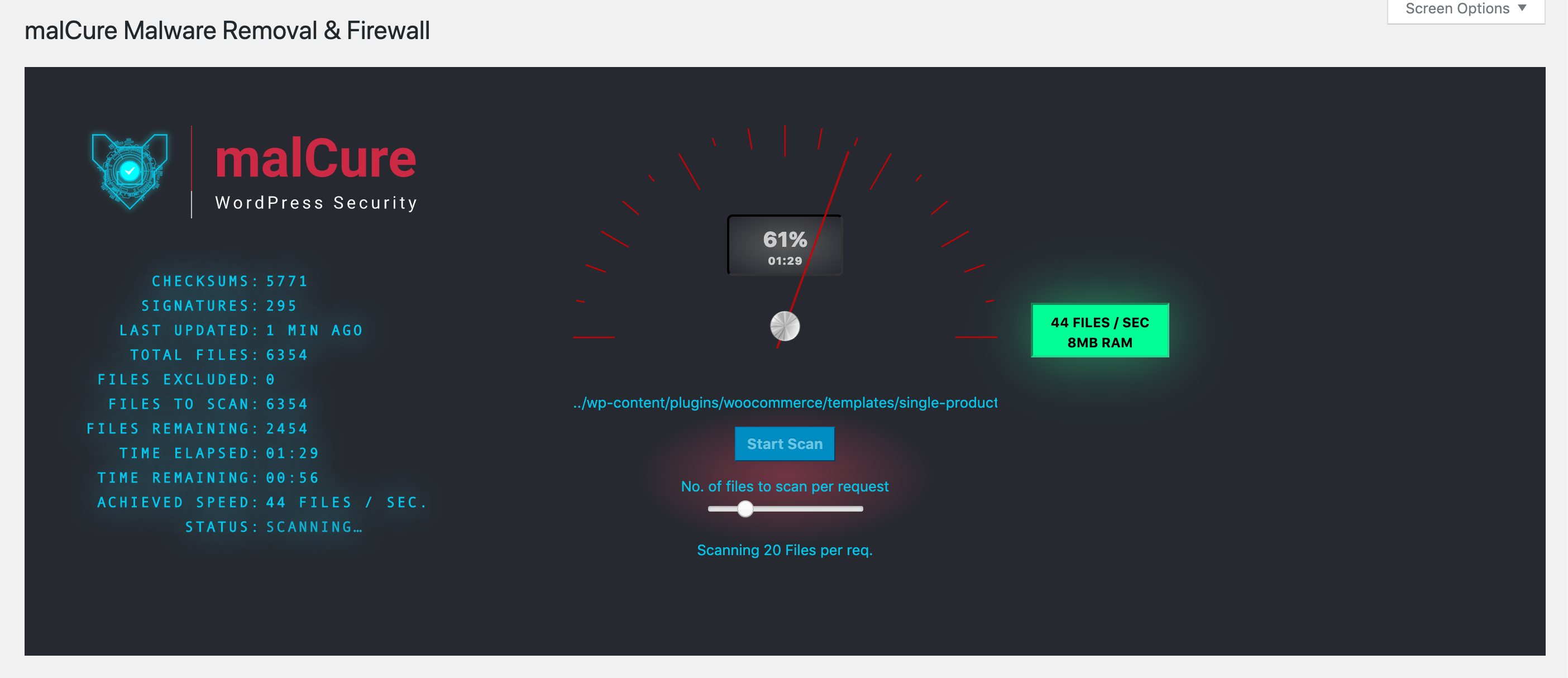
- Once the scan completes, it will report the results.
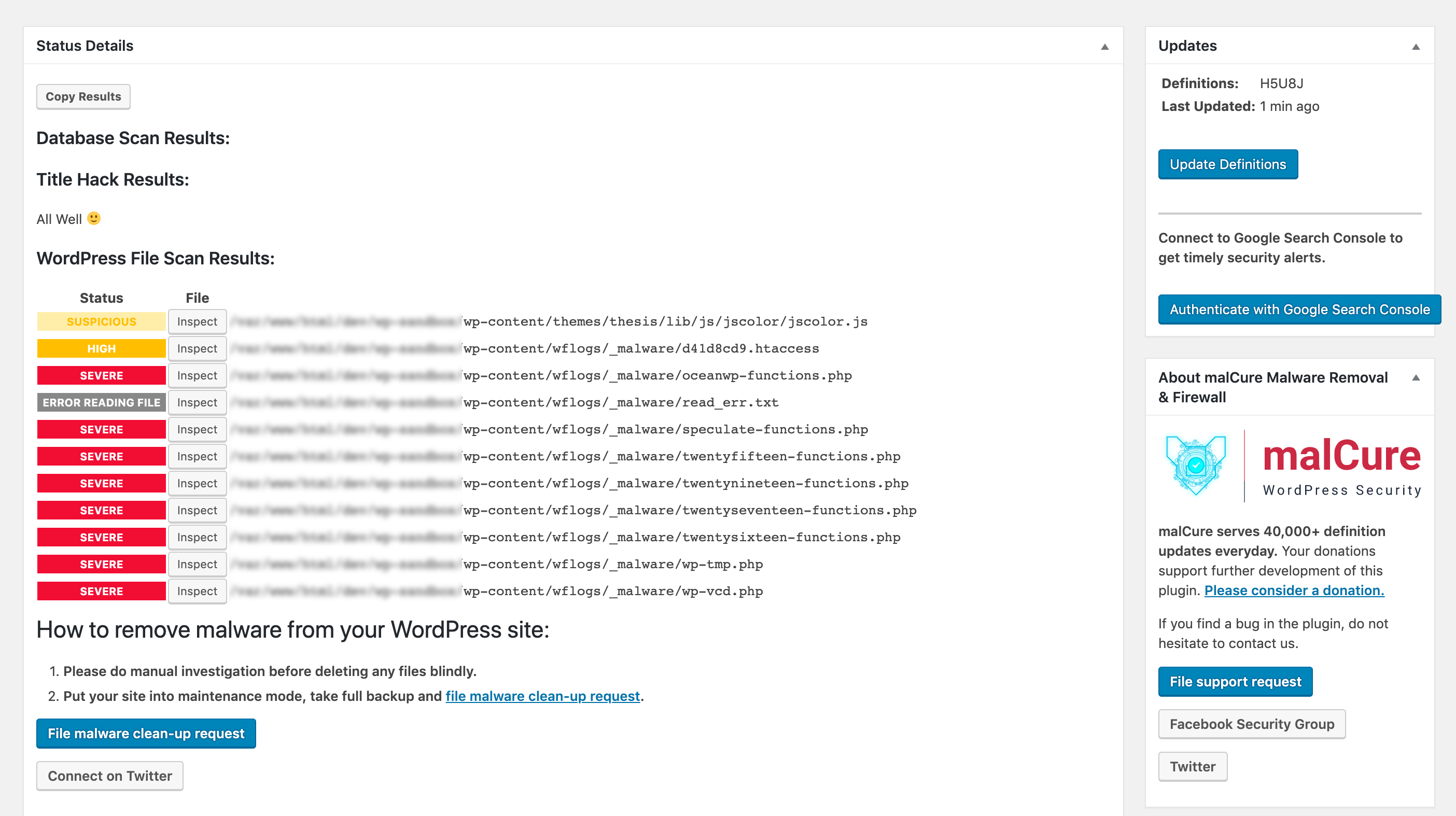
- The “Inspect” button will allow you to review the files (if the file is readable / accessible).
- Finally we get to the cleanup part. On your website, there are several types of files:
- WordPress Core files: Files in the WordPress installation root and files inside
wp-contentandwp-includesdirectories. - Plugin & Theme files
- Uploads: Files inside
wp-content/uploads - Other miscellaneous files.
If a WordPress core file is infected, you need to replace it with the original. To do you, you need to download the exact WordPress release, extract and upload the clean file to overwrite the infected one. The same goes for themes and plugins.
If anything else in uploads or any other file is infected, you need to decide if it can be cleaned up or can be removed. Do backup your files before you execute any irreversible action.
- WordPress Core files: Files in the WordPress installation root and files inside
4. Root Cause Analysis
Before we lock-up, we really need to identify how the malware got into the website at the first place. Most of the time it is due to software misconfiguration — outdated software. Check that your server software is secure, WordPress, plugins and themes are up-to-date. Check out https://wpvulndb.com/ to see if there’s any recent vulnerability issue detected with any plugin or theme.
5. Securing your WordPress Site
Finally, inspect all WordPress users. Verify that no account has been hacked. Reassess accounts and privileges. Shuffle the salts to logout all the logged in users.
The malware could have easily resulted in a data leak. It can read wp-config.php and could have leaked your database password. It’s a challenge to fathom the spread of breach. It’s time to update all your passwords: CPanel, FTP, MySQL, WordPress and any other applicable.
Once this is done, you need to watch out for reinfection. When you lock out the bad guys, they get peeved off. Also they know that your site was vulnerable and they will test this. There are good chances that the amount of spam and bot requests will increase. If you feel that you need professional help with this, feel free to reach out to us.