
Seen this dreaded This site may be hacked message about your own site in Google Search?
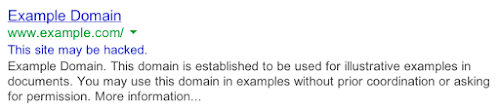
Sure you want to know how to clean malware from wordpress site. Read on.
It was about the end of the year 2008 when one of my clients reported the dreaded message “This site may be hacked” in the search snippets for one of her sites. A quick visit to Google Search Console confirmed that this wasn’t done in error. The client had verified everything (to the extent she could verify things) and had submitted a reconsideration request to Google. It was declined.
She had been talking to the hosting support. An agent attended to the chat in 25 minutes and escalated the issue to the security team. The security team mailed her asking for more information and put the ticket into pending.
It had been hours and she wanted professional intervention. I took over, chatted with the support, they did a malware scan, found nothing and closed the ticket as resolved.
This wasn’t just some “yet another cheap hosting company”. They are in the list of the most respectable and trusted hosting providers.
Well if that’s all that the hosting support can do, then matters need to be taken into your own hands. Let’s clean hacked wordpress site, shall we?
- Before you begin, you must have the most important skill: patience.
- Read some. Here’s the first one you should read about WordPress infection.
- Decide if you want to do it yourself of you want to hire someone. Regardless of what others will tell you, most malware cleanups recur within no time without raising any red-flags. Prepare to be thorough and keep a close watch.
Table of Contents
- Symptoms of Malware on a WordPress Website
- Precautions to Exercise While Examining Website for Malware
- How to Clean a Hacked WordPress Site
- Disable your website and block it all
- Backup as a precaution
- Identify the issue & Clean WordPress Malware
- Identify the scope of affect
- This Site May Be Hacked WordPress How To Remove — Fixing the issues
- Root-Cause-Analysis & Finding Security Loopholes
- Verifying That The Site is Clean and Accepted
- Preventing Attacks in the Future
- Summary
Symptoms of Malware on a WordPress Website
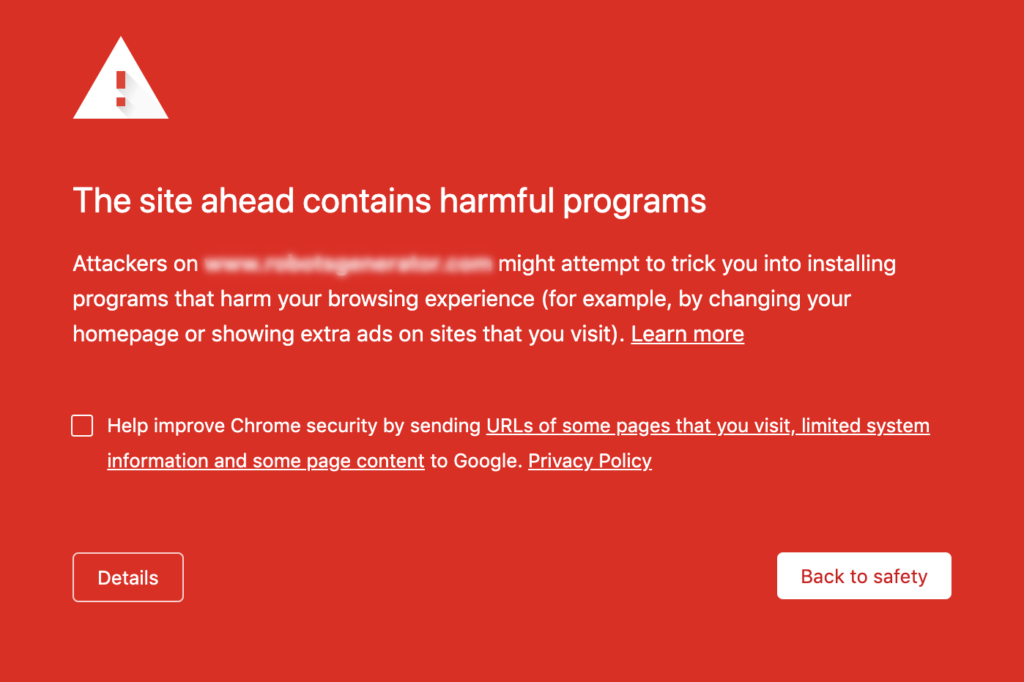
A couple of IoC’s that are clear indicators of a hack include:
- Your WordPress website is redirected (for example JavaScript Redirect Malware).
- Website is blacklisted by McAfee, Google, Norton or other blocklists.
- Website has been flagged for distributing malware, like a ban on your Google Ad campaigns etc. due to malicious software or similar.
- Website visitors report about their antivirus flagging your website as malicious.
- Browser throws a malware or site attack warning when you try to visit that URL.
- You receive a Google Search Console message saying your website is hacked, deceptive site ahead, this site contains harmful programs or this site may harm your computer (check this article on how to remove Google blacklist warning and notifications).
- Your web-host blocks your account (and here’s an article about cleaning a website blocked by the web-host).
- Strange URLs loading in the browser status bar when loading your website.
- A rogue user registers on the site and posts malicious content / PDFs. Case Study: This Hack Will Nearly Kill Your Online Business
- Other unwanted behaviour like new administrative users etc.
Precautions to Exercise While Examining Website for Malware
- Do not visit your own website. Certain types of malware (silently or visibly) trigger malicious downloads or can redirect you to rogue websites including adult website or ones related to drugs etc.
- Preferably use a virtual machine to examine the website.
Having a virtual machine is a security safe-guard that limits the security issue to the virtual-machine and keeps your actual system safe. A virtual machine is the difference between some blogger preaching on how to recover your hacked website versus a professional trying to recover another hacked website on one fine day. Don’t be another victim to your own hacked website. You have to remedy it.
How to Clean a Hacked WordPress Site
Disable your website and block it all
The first step in troubleshooting a hacked website is to disable your website. Disable could mean many things. A good web host by default would block the website. This has a two fold purpose:
- Stop the infected website from being publicly view-able. An infected website may be defaced and could infect the computer system of visitors.
- Stop the hacker from doing anything further. Once the website is offline, the hacker wouldn’t / shouldn’t have access to it, thus limiting the extent of damage already done.
- Save the face of your brand. Your SEO as well as the trust users have in your site goes for a toss as does the brand-name.
What exactly does blocking mean and how to block your website
- Take a pen and paper. Trust me, you are going to do quite a lot and you want to note everything down. You can use your computer system to take notes and screenshots but there’s quite nothing like pen and paper if your battery goes down or the kids spill a glass of water just when the world is about to go down. Point-wise note down everything you are doing. I’ll expand on this later.
- The first thing that you should do is to put your website into maintenance mode. You can use the excellent WP Maintenance Mode plugin by Designmodo. This disables public access to your website. But you are not done yet. You’ve barely gotten started.
- Your hosting provider would have given you some sort of access to a control panel. It could be VirtualAdmin, Webmin, cPanel, WHM, etc. You now need to limit the backend access to your site.
- Update your password to the control panel. Note it down on paper for now. We’ll change it again later. Think of something at least 8 characters and easy to remember. I recommend the mnemonic password generator that gives you easy to remember yet strong passwords: something like this:
cat_!dead?meansthe cat underscore is not dead. - Identify who has access to the hosting. Often you may have multiple users who have access to the hosting account. You will need to revoke their access at least temporarily.
- Change the password for mysql / mariadb, phpmyadmin, ftp, ssh and WordPress admin backend. I can’t cover the exact steps as this would vary depending on your hosting provider. Note down each new password and where it belongs.
You don’t want anyone else to be getting into the server while you are working.
Backup as a precaution
It’s obvious that now is not a good time to backup. But you still need a backup. This is for several reasons:
- This is the latest backup of your site with the most recent posts, pages and other data.
- This backup also has the proof and evidence of the security issue at hand, which you can use to study things later and do a root-cause-analysis.
- This also is the latest backup in case things go south and we need to recover stuff.
Don’t keep this backup on the server. Download it to your virtual machine.
There are three parts to backing up WordPress.
- The WordPress files which includes all your images, plugins, themes etc. For this you can use Filezilla. Make sure to backup .htaccess (a hidden file). It’s used for pretty permalinks, caching, redirection and several other directives.
- The WordPress database. For backing up the database you can go to the backend of CPanel (or which ever control panel you are using) or you can do it via phpMyAdmin.
- Verify that the files have been properly backed up. The backup archive can be verified by most archive managers and the database dump can be verified by checking the end of the sql dump.
Note: You can also use a backup manager to do this job for you but they can be tricky to use, can silently fail during the backup, do an incomplete backup or fail while restoring. I don’t trust any backup manager.
Identify the issue & Clean WordPress Malware
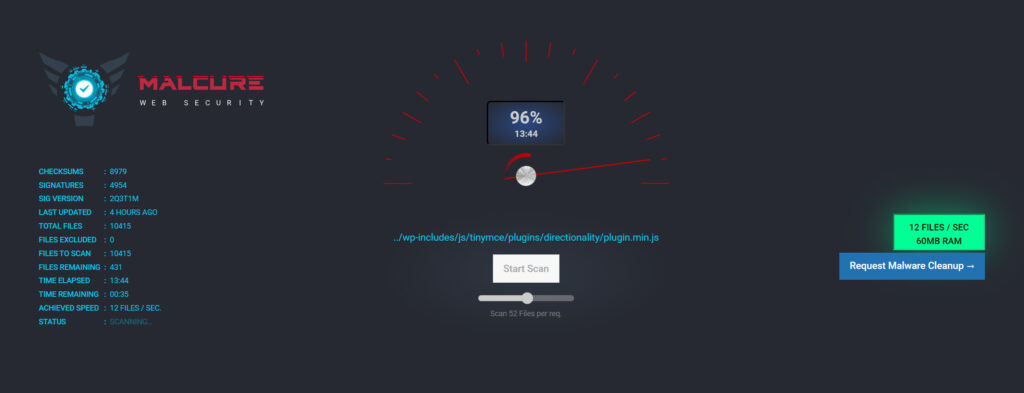
So what exactly is the issue? This is the most challenging part and much depends on your technical aptitude as well as understanding of the issue and approach. There are several ways you could identify the problem to clean WordPress malware.
- The source of the webpage: If that’s how Google detected it, then the evidence will be here. Check the html source of the webpage. It’s quite possible that only a few web pages are affected and it’s totally possible that the entire website is affected. So pick a URL where the issue is reported. It may not be evident and obvious so look carefully. Scan each line and look for issues (yes it’s vague but that’s how a professional will try to smell things). Do not forget to check all JavaScript files that are included in the webpage. You may like to use online website malware scanner to quickly scan HTML source code of your site.
A word of caution: There are situations wherein the infection may not be obvious or may not be present on the webpage at all. For example malware that only hijack traffic coming from search-engines will not show on the site unless you visit the site from a search-engine. At other times, some malware only render for specific user-agents like mobile or a specific browser. - What all is loading: Sometimes the issue may not be obvious from the source-code of the webpage. The browser’s built-in developer tools come in pretty handy. Open up the browser tools panel and go to the Network tab. Load the website and look for what all is getting loaded. We are looking for anything loading from external domains in particular, but keep an eye out for anything that looks suspicious on the local domain too.
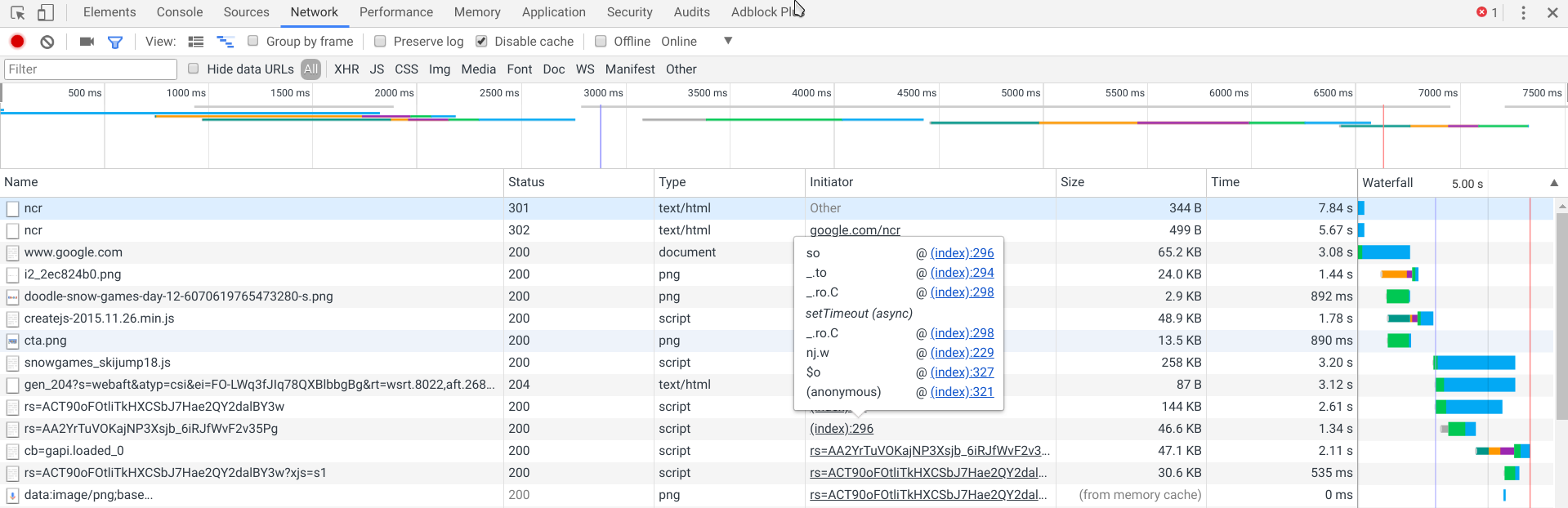
- The included scripts: Cross-site Scripting (XSS) Attack is one of the most common attacks. This attack basically modifies one or more JavaScript files on your WordPress install which tends to load up things. The JavaScript would then dynamically load a hidden iframe etc. to download malware to the visitor’s machine. Of all the JavaScript files available on the server, you just have to scan the ones that are included on the target page (at least initially).
- Looking for more similar infected files: If you have shell access to your hosting (it depends on the kind of hosting are you running) then it should be a simple matter of running a grep command to scan all files for that particular string.
- Inline scripts and content: Regardless of whether or not you found a rogue script, you will need to scan the website and see if there’s something in the database too. You can use phpmyadmin or the mysql command-line to search for strings like
iFrame,noscript,base64or evenevalanddisplay(which you’ll find many and most would be legitimate). - Run an automated malware scanner: It’s difficult for automated scanners to pick on JavaScript and database malware since the issue is not with the content of the script or the content of database itself. The issue is with the rogue external malware site that it is loading it. But remember you have to be thorough. Don’t leave anything to chance while you are at it. An in-depth scan of the website will list out all the infections present on the website. For this you can use a malware scanner provided by your webhost like ClamAV. Or you can use a WordPress malware scanner plugin like Malcure Malware Scanner or Malcure Advanced Edition. It will list all the infections found in the database as well as in the files. Also scan your desktop OS for anything that you find suspicious.
- Manually inspect .htaccess, files inside wp-content folder, files inside your active theme, inside plugins, must-use and drop-in plugins.
- Look inside the database for any injected scripts.
Identify the scope of affect
Hopefully by now you have identified the issue. Correction, hopefully you’ve identified something by now. But it is only a symptom. You need to correlate your findings and identify if the breach was limited to a single site, a single hosting account or at the operating-system level. Only then you’d know what all to fix and how to fix it.
This Site May Be Hacked WordPress How To Remove — Fixing the issues
Depending on what you’ve identified, it would be trivial to replace the infected / affected JavaScript files and / or fix the actual content of WordPress posts and widgets etc.
Clean up the infected files, over-write with original ones. Remove plugins and themes that you don’t use. Update all plugins, themes and WordPress. Newer versions of software almost always have security fixes to discovered vulnerabilities.
However don’t be in a rush to make the site live. We are forgetting the heart of the problem — how did it get in at the first place?
Root-Cause-Analysis & Finding Security Loopholes
While a complete list of security loopholes is impractical to cover since everyday new loopholes are discovered and it’s basically a catch-up game before the bad guys innovate something new and then the good guys plug-in the hole; a root-cause-analysis will:
- Help you identify the attack vector (how it happened) and fix the root-cause of the problem so that it doesn’t repeat; again.
- Give you valuable insights on the system and security internals.
I’m however listing some of the most common attack vectors:
- Allowing (unauthenticated) user-upload of files.
- Allowing user-upload of unsanitized data / rogue plugins serving unescaped data.
- Some rogue script that your web-developer left over when migrating your WordPress website.
- Some clipboard content that automatically got pasted when copying text over from some other webpage and included inline script(s).
- Too many users, accounts with access to your hosting / WordPress / FTP / SSH.
- Easy to crack passwords.
- Mis-configured server that misbehaves or leaks confidential information contained in PHP files.
- Rogue WordPress Theme or Plugin.
- Hidden plugin (must-use plugin) that does mischievous things.
- Unknown users with special privileges inside WordPress.
An Example of Malware Root-Cause-Analysis
I can’t even begin to list what all ugly hacks exist there. But for this specific case, it was a base64 encoded piece of script. The catch was that it was encoded 10 times. So every time I decoded it, I didn’t see anything which I could make sense of… not until I decoded it 10 times. And even after that, the hacker was smart enough to use a piece of packed code that looked just cryptic and rubbish.
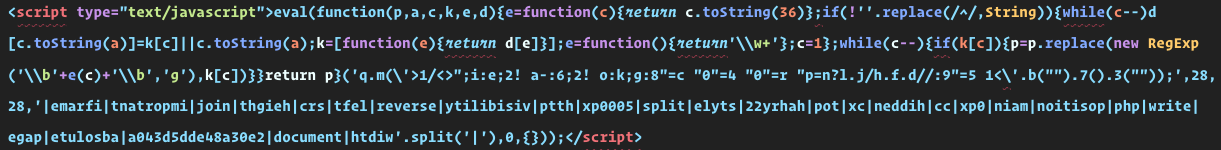
Let’s see if we can make sense out of it:
Fourth line from the top: emarfi is iframe with the characters reversed. tnatropmi is important, xp0005 is 5000px, so on and so forth.
So cool! Huh? The code was being passed into a JavaScript eval call.
After some clean up and fixing, while going through the URLs I came across a URL which had a form for attachments. I’ll not go into the specific details and teach you how to duplicate this and hack someone’s website though.
Verifying That The Site is Clean and Accepted
- Once you have made sure that there are no security loopholes open and review that your server is configured right, website is clean and ready to go live, run it through malware scanner again. With Malcure Malware Scanner you can scan all core files for integrity and all files for malware. You can also inspect any suspicious files.
- You can now make it live and submit a reconsideration request. Do not add any new users or allow anyone other than yourself to have privileged access. Give yourself 48-72 hrs. and watch out for any troubles or recurrence.
- If you don’t use Google Search Console, you’ll need to register and verify your site in Google’s Search Console.
- Sign in to Search Console and go to “Security & Manual Actions” → “Security Issues” section.
- Go ahead and “Request a review”. Once Google verifies that your site is clean and isn’t infected anymore, they’ll remove the “This site may be hacked” message.
- Later when all seems to be going well and there are no more issues reported with the website, it’s time to take a backup.
- Now finally you can change the passwords once more to something strong, that’s not written on a piece of paper and you can add other users who need access to the website, hosting etc.
Preventing Attacks in the Future
While it sounds contrary to the popular word out there, as an information security consultant, I personally do not recommend any third-party plugins or scanning services — they charge monthly, send cryptic notices about security issues and play on FUD: Fear Uncertainty Doubt ending up confusing users forcing them to buy useless stuff. Installing plugins that list the security gaps is good. However you’ll need help of a professional who can make sense of the security messages and help you rectify them. Hardening WordPress installs is something that you should entrust to a professional (and not a self-proclaimed one). With a well-maintained security infrastructure, you wouldn’t need to worry about much.
- Keep your accounts secure. Passwords can be stolen from emails, stolen phones and what not.
- Keep your hosting server properly configured with a well-secured firewall and other security infrastructure.
- Don’t leave rogue data, files, forms on the server. They can be used for various types of attacks.
- Keep your WordPress installation, themes and plugins updated. This has the additional challenge of keeping the environment stable and compatible.
Additional Resources:
- Sucuri’s Guide: How to clean hacked WordPress
- Ask WP Girl: 10 Steps to remove malware from your WordPress site
- Live WordPress Malware Infection Removal & Analysis
Summary
Sites get hacked all the time. It’s important to know what do to and how to do things because security issues like this are a time-sensitive matter. Too late and loss increases exponentially. You can’t afford to “try” things and “see if it works out”. So here’s my advise:
- Maintain regular backups of all the website files including database.
- Harden your WordPress install.
- Don’t neglect the Google search console.
- It’s not a matter of “if” but rather when you’ll be affected.
- Keep your calm, get professional malware assistance and don’t try things unless you want to mess up with the database and Linux utilities.
- Keep a close watch after things are back in place.
Hope this post helped shed some light on what it is to recover from a hacked WordPress website. If you need help, Malcure is only an email away.